Ransomware Gang Adds Insult To Injury By Reporting Victim's Security Breach To The SEC
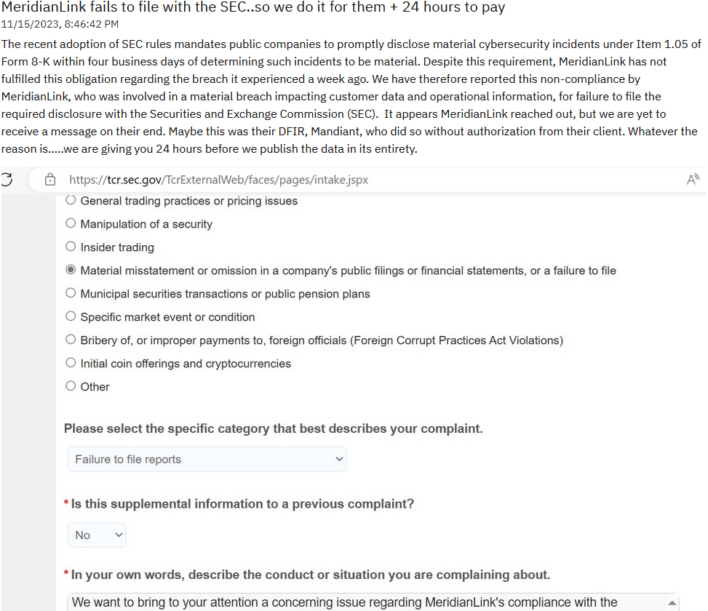
Yesterday, ALPHV posted that it had breached MeridianLink, a software-as-a-service (SaaS) company in the financial sector whose products power digital loan management, among other solutions. That initial post was seemingly taken down and replaced with what surmounts to a scare tactics blog post explaining that the group is giving MeridianLink 24 hours to pay up or have the compromised data published on the group’s Tor website.
ALPHV also notes that given SEC rules regarding the disclosure of cybersecurity incidents, the group has filed a complaint with the commission. The blog post explains that “SEC rules mandates public companies to promptly disclose material cybersecurity incidents under Item 1.05 of Form 8-K within four business days of determining such incidents to be material.” The group subsequently claims that MeridianLink did not follow this new rule and, as such, “reported this non-compliance.”
Despite ALPHV’s SEC complaint and statement, it is unclear whether the new reporting rules are in effect at the time of writing. According to the Federal Register’s published final rule from the SEC, “With respect to compliance with the incident disclosure requirements in Item 1.05 of Form 8–K and in Form 6–K, all registrants other than smaller reporting companies must begin complying on DECEMBER 18, 2023.” The other time frame for when Form 8-K would go into effect would be 90 days from publication in the Federal Register, which is on December 2nd given the effective date of September 5th, or September 2nd given a publication date of August 4th.
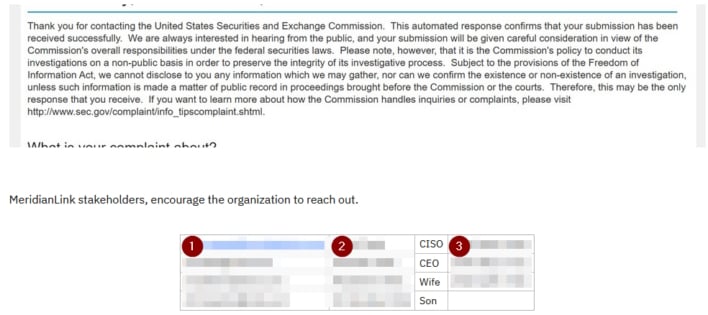
In any event, this demarcates a new type of thuggery and hooliganism from threat actors trying to push victims into paying up or facing the wrath of Uncle Sam. This may not be how the system was intended to be used, but we are here now. Moreover, it would appear that ALPHV has also published the contact details of Meridian’s CISO, CEO, wife of the CEO, and son of the CEO as part of this campaign. That is pretty despicable, as even though stakeholders have a right to know about a breach, it shouldn’t necessarily come at the cost of being doxxed.