Beware Of Hackers Using Fake Browser Windows To Steal Your Steam Credentials
Some recent Steam account phishing attacks try to lure in unsuspecting users with private messages offering discounted esports event tickets, opportunities to join esports tournaments, or the chance to vote for a user’s favorite esports team. Some threat actors set up gaming livestreams similar to the recent cryptocurrency scam livestreams. Rather than offering free cryptocurrency, these gaming livestreams advertise free in-game character customization items. All of these different offers include links to websites controlled by threat actors. These websites are made to appear legitimate and direct users to claim an offer by logging into Steam. However, the Steam login windows that appear when users follow these prompts are not real windows.
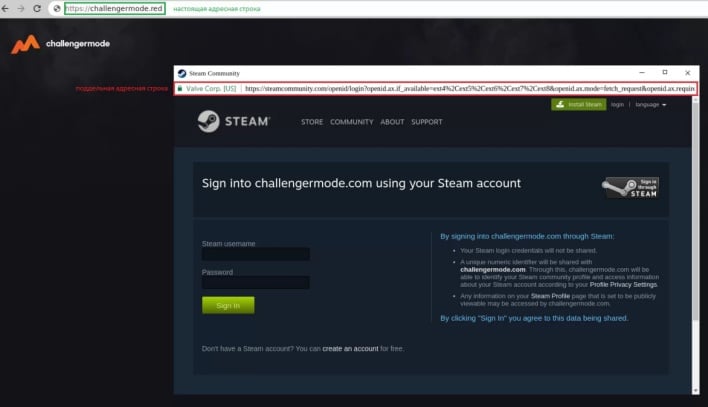
BITB attacks have now graduated from proof of concept to reality, as threat actors are using this technique in their phishing attacks on Steam accounts. The image above shows an example of an interactive fake Steam login window on a phishing webpage. Users can move the window around inside the confines of the web browser and change the language of the login page. The fake page can detect if a user's account has two-factor authentication (2FA) enabled. If so, the window will update with a prompt asking for a 2FA code.
All login credentials entered into this fake window are sent to the threat actor’s command-and-control (C2) server and relayed into Steam, giving the attacker access to users’ steam accounts. In order to avoid falling victim to a BITB attack, users can perform multiple checks to see whether login windows are real or animated. Real login windows will appear in the taskbar, have the same window design as the parent browser, and have a functional address bar. Users can also try minimizing the window to the task bar or moving the window outside of the browser. A fake browser window won’t be able to perform either of these actions. Disabling or blocking javascript is another defense against BITB attacks, though doing so will usually hinder legitimate login portals as well.

