BITB Phishing Technique Creates An Animated Window To Steal Your Passwords
Phishing attacks trick users into revealing sensitive information or installing malware by presenting users with messages or web portals that appear to come from legitimate authorities or services. Earlier this year, we covered the prevalence of phishing attacks that take on the guise of the international shipping service DHL.
Phishing attacks like the DHL attacks begin with an email that contains a link to a website that looks almost exactly the same as a real site. However, while the fake site may look legitimate, users can often detect it as fraudulent by looking at the site’s web address. Websites used in phishing attacks usually make use of web addresses that may appear the same as the web address of a real site at a glance, but that don’t hold up under scrutiny. Users can sniff out phishing attempts by looking in the address bar for numbers substituted for letters, as in the case of m1cr0s0ft.com, or other modifications to the web address of a legitimate site.
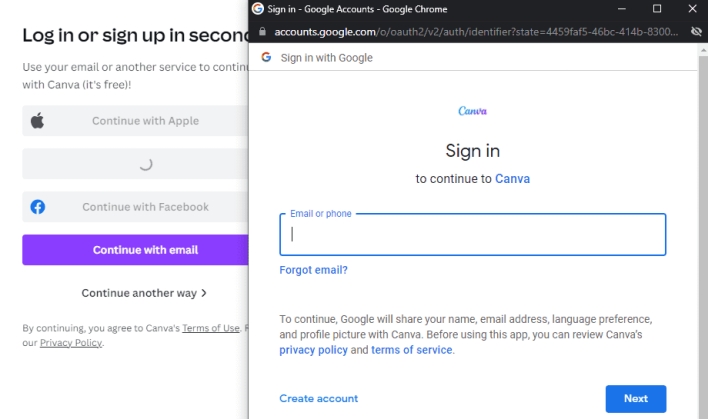
Once users click the “sign in” button, a new browser window opens where users can sign in. This new browser window isolates the sign in process so that the website using OAuth never sees users’ sign in credentials. Isolating the sign in process is a desirable security and privacy measure, but a security researcher has shown that bad actors can mimic this particular isolation technique to hide phishing attacks.


mr.d0x’s article detailing BITB also shows how bad actors can obscure the real destination of a hyperlink using JavaScript, meaning that hovering your mouse cursor over a hyperlink to determine if the destination is legitimate is not an effective way to detect phishing attacks so long as JavaScript is enabled. Both of the techniques for obscuring phishing attacks presented in the article make a strong case for the usefulness of tools like NoScript that can selectively disable JavaScript elements.

