AMD Rolls Out Patch For Alarming EPYC Microcode Vulnerability Affecting Zen 1-4 CPUs
Importantly, AMD's announcement does not mention any impact on consumer Ryzen CPUs, including desktop and laptop processors, as well as PRO and Threadripper models. As of now, only EPYC server processors appear affected, but given AMD's history with security flaws—such as the Ryzenfall vulnerabilities from 2018, which similarly targeted firmware integrity—it’s understandable that users might be wary. Whether this issue has any broader implications for AMD’s consumer lineup remains to be seen.
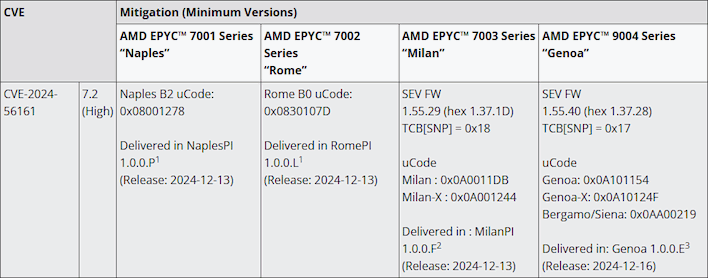
Google plans to release additional details about the exploit on March 5, but a proof-of-concept payload is already available on the Google Security Team GitHub page. AMD has also published its own security advisory, listing all affected processors and detailing the required mitigation steps, which involve updating microcode and firmware. Users and administrators should apply the latest patches as soon as possible. More information can be found on AMD’s official security page here.


