Zero-Day Exploit Affecting All Latest Windows Versions Causing Blue Screen Of Death Is Live On Github
Given the severity of the exploit, the U.S. Computer Emergency Readiness Team (US-CERT) has already published an emergency advisory, officially labeling it VU#867968. US-CERT describes the memory corruption vulnerability in detail, noting:
Microsoft Windows fails to properly handle traffic from a malicious server. In particular, Windows fails to properly handle a server response that contains too many bytes following the structure defined in the SMB2 TREE_CONNECT Response structure. By connecting to a malicious SMB server, a vulnerable Windows client system may crash (BSOD) in mrxsmb20.sys.
A vulnerable system can be subject to a Denial of Service (DoS) attack which then results in a Blue Screen of Death (BSOD):
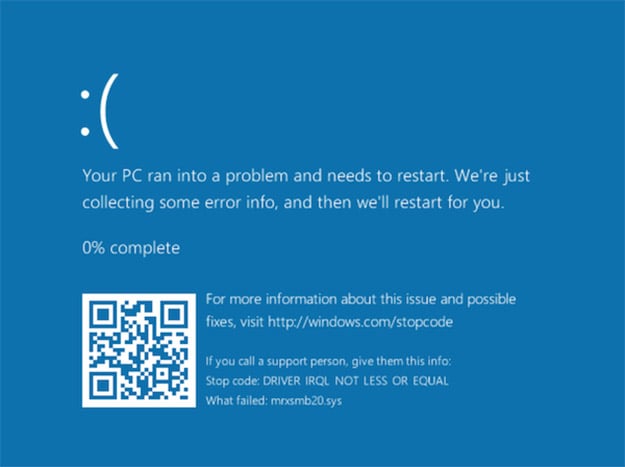
According to Johannes B. Ullrich, Ph.D., Dean of Research for the SANS Technology Institute, “It isn't clear if this attack is exploitable beyond a denial of service.”
@PythonResponder quick and dirty gif pic.twitter.com/ccwrrG36rO
— Chris Mallz (@vvalien1) February 1, 2017
It was originally determined that the exploit affects both Windows Server 2012 and Windows Server 2016, but @PythonResponder verified that fully patched versions of Windows 10 are also vulnerable. The US-CERT further confirmed that the vulnerability crashes Windows 10 in addition to the legacy Windows 8.1 operating system.
At this time, there is no official fix from Microsoft, although US-CERT suggests that admins block “outbound SMB connections (TCP ports 139 and 445 along with UDP ports 137 and 138) from the local network to the WAN.” However, given that the exploit is out in the wild, we have the feeling that Microsoft will be issuing a patch rather swiftly. For those that are curious, you can find the exploit here.
Image, credit: Wikimedia user Byseyhanla


