Urgent High Severity Security Backdoor Found In Popular Linux Utility
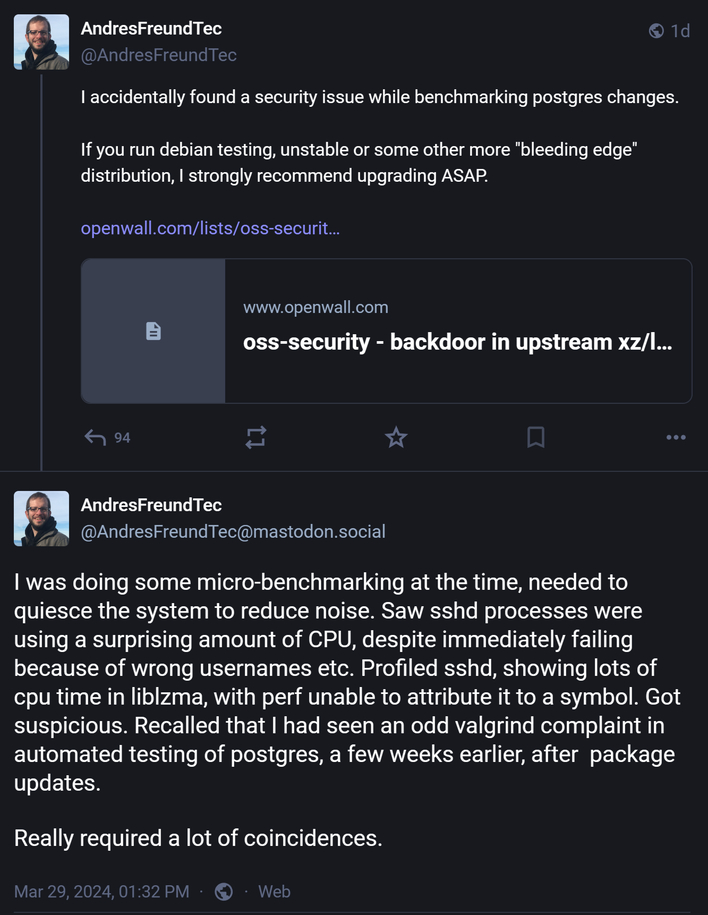
On March 29th, Microsoft engineer Andres Freund posted that he was doing some micro-benchmarking on his systems. In this testing, he noticed that the sshd process was using a lot of compute resources and that logins via SSH, a command line remote access protocol, took about .5s more time than before. Upon this discovery, he dug deeper to find that most of the compute time was spent on something called "liblzma," which is a part of the xz-utils package. This began a thread-pull, unraveling a highly obfuscated backdoor in xz-utils, put in place by an unknown threat actor named “Jia Tan.”
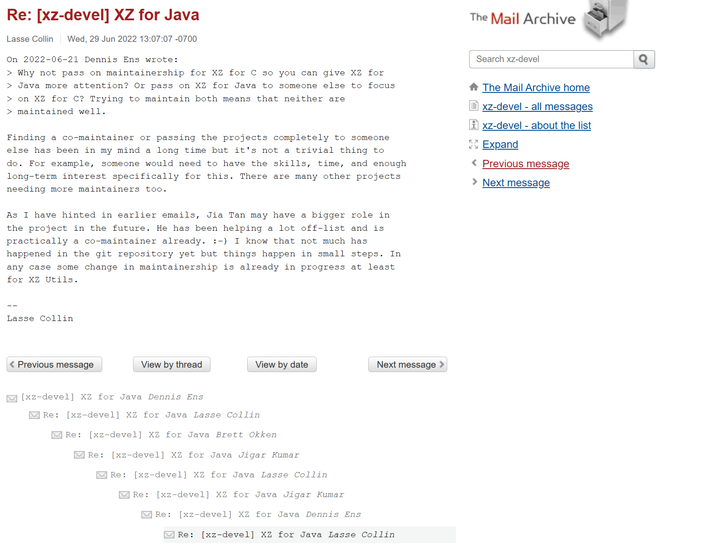
While many folks are covering how the vulnerability affects people and how it works, including Freund, the more interesting details lie in how this happened in the first place. According to Evan Boehs, who is one of a few folks untangling this mess, Jia Tan created a GitHub account in 2021 and began to make contributions that were a bit suspicious to different projects. In 2022, Jia Tan submitted a patch to xz-utils with a now-established contribution profile. While the patch was nothing major, it led to a conversation with the owner of xz-utils, Lasse Collin, where he was pressured to add another maintainer to the project as the project was not being taken care of as adequately as it should have been. In retrospect, these are social engineering tactics with multiple individuals applying urgent pressure to someone who was quite concerned about their project.
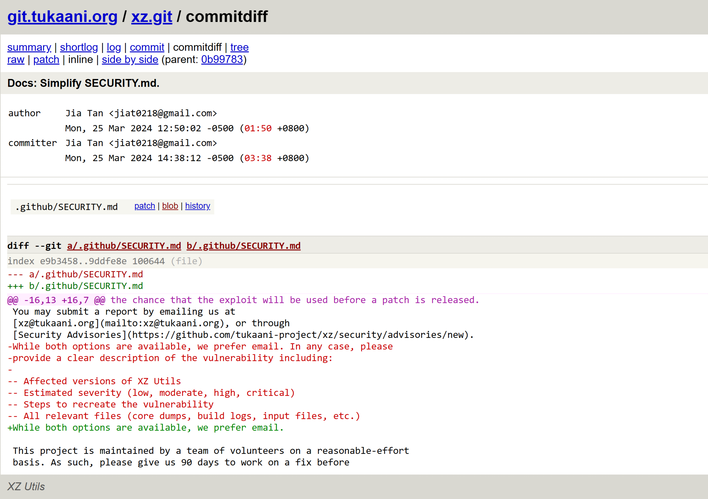
In any case, Collin added Jia Tan three days later as another XZ project maintainer, allowing this person to add code and become a regular contributor. Over time, Tan became a more trusted figure in the project, and signs indicate that Tan had increased control over xz-utils. All these events coalescing allowed Tan to implement the final components of the backdoor with some test files added to the code base. There was also a sudden push for this malicious code as part of xz-utils to be included in operating system releases like Debian and Ubuntu coming from Tan. However, it all came crashing down like a house of cards when Freund pulled on the thread, which started with noticing slightly longer times for SSH logins.
At the end of the day, it seems the head maintainer of the XZ project was, through years of work and communication, social engineered. Jia Tan does not appear to be a real person and rather seems to be an amalgamation of names that would sound Chinese, but it is wholly unclear. Many people also suspect that there is a nation-state behind this ordeal, and this was an attempt at setting the groundwork for some rather nefarious and near-undetectable things. Of course, our thoughts go out to Collin Lasse as he now has to work through this trouble and figure out next steps.