Cloud Gaming Service Discloses Data Breach Affecting Over Half A Million Gamers
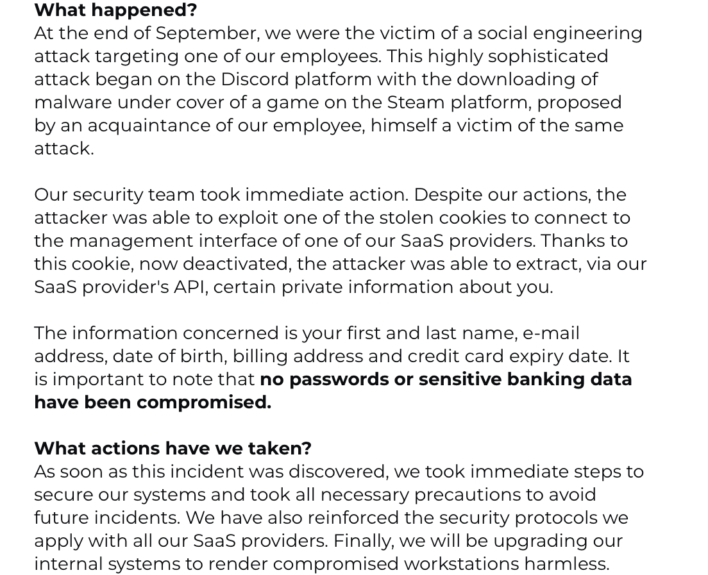
Over on the ShadowPC subreddit a couple of days ago, users were posting notices they had received explaining that Shadow had suffered a breach and customer data was compromised. The notes explain that at the end of September, an employee was the victim of a phishing campaign through Discord, wherein the employee downloaded malware that was fronting as a game on Steam. This malware then compromised the employee’s cookies, which allowed the attacker to connect to the “management interface of one of [Shadow’s] SaaS providers” and “extract, via [Shadow’s] SaaS provider’s API, certain private information.”
After this breach was discovered, Shadow locked down its systems and turned off the cookie to prevent the attack from continuing. Further, the company is reinforcing security protocols and moved to upgrade internal systems to “render compromised workstations harmless.” However, Shadow still recommends that customers who might be affected be vigilant about any emails they receive, as they could be phishing attempts. Further, it is recommended that users implement multi-factor authentication (MFA) to help protect themselves, especially on their Shadow accounts.
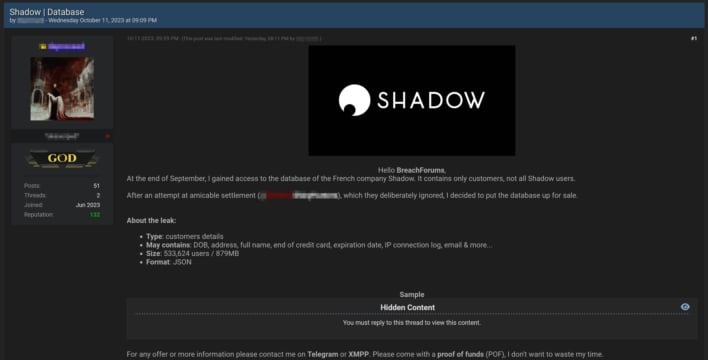
Curiously, this all lines up with a post to BreachForums from a user who claims to have gained access to the database of Shadow customers. They note in their post that there are 533,624 customer records which may be associated with birthdates, addresses, full name, end of credit card, expiration date, IP connection information, and more. It is still being determined whether this bundle is legitimate, but given the timing, we are inclined to think there is some stolen data there.
In any event, this is a good opportunity to remind people that having good cybersecurity hygiene also involves the end user, as humans are nearly always the weakest link. You never know if a link sent by a friend is legitimate, because that person could be compromised themselves, as was the case in the Shadow incident. Thus, always "trust but verify" links and files, as it only takes one bad click for you to fall victim.