Many websites and applications employ various device fingerprinting methods to identify users and track their activity across websites and applications over time. The
Electronic Frontier Foundation has a good
explainer on this subject, as well as a tool to test how well your browser protects you from fingerprinting. TorZillaPrint from arkenfox is another good fingerprint testing tool. Both of these tools use a number of tracking methods that are currently in use on the web. However, researchers are continually developing and testing new methods of digital fingerprinting.
A team of researchers from multiple universities recently published a paper detailing a new method for
fingerprinting users by uniquely identifying their GPUs. Some fingerprinting techniques make use of device hardware information, but this new technique is special in that it is able to distinguish between identical
GPUs, meaning this method can differentiate users with identical hardware and individually identify them. The researchers dubbed this new technique DrawnApart.

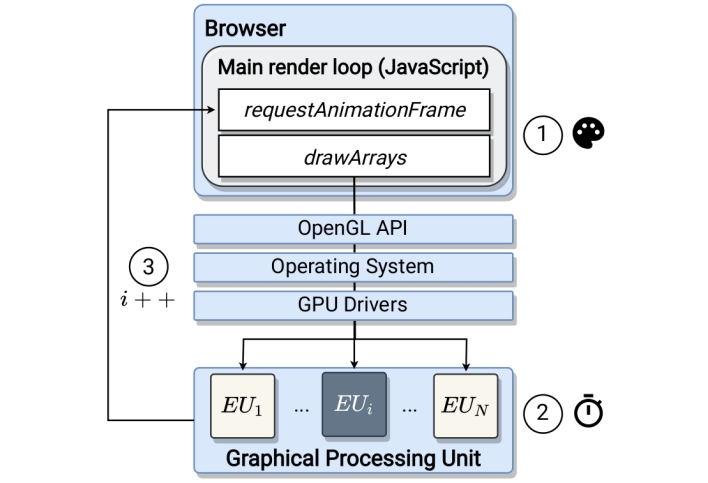
The technique takes advantage of manufacturing differences between identical GPUs, as no two GPUs are exactly the same, even if they share the same name and architecture. The researchers developed a script that makes use of Web Graphics Library (WebGL), which is used for rending 3D graphics in-browser. DrawnApart relies on WebGL’s ability to run GL Shading Language (GLSL) code to instruct users’ GPUs to execute short GLSL programs, targeting specific execution units within the GPU. The script makes note of variations in speed between the different execution units and uses these timing variations as a device signature for individual GPUs.

The researchers tested this technique in a lab setting with 88 devices, as well as in the wild on 2,500 crowd-sourced devices over the course of several months. The technique worked in both settings to identify integrated and discrete GPUs in desktop and mobile applications. The researchers integrated this technique into a larger state-of-the-art tracking algorithm and found that it increased the median tracking duration by up to 67%, boosting average fingerprint effectiveness from 17 to 25.5 days on the low end and 18 to 30 days on the high end.
The
research paper lays out three specific countermeasures for
DrawnApart. The first is preventing parallel execution by limiting each webpage to a single execution unit in the graphics stack or completely disabling hardware-accelerated rendering. Unfortunately, current graphics APIs do not support such execution unit limitations, and, even if they did, WebGL is built to rely on parallelism, so usability and responsiveness would be severely hampered. The second proposed countermeasure is preventing deterministic dispatching by the addition of a randomization step in the GPU’s dispatcher. This countermeasure would avoid the performance hit, but would not fully block DrawnApart’s fingerprinting, as a permuted trace still contains data about the system. The final countermeasure is preventing time measurements, but the paper notes that completely blocking timing measurements from the web isn’t a realistic possibility.
The paper also discusses the use of filter lists, like those employed by Brave Shields and extensions like Ublock Origin, Ghostery, and Privacy Badger. These filter lists block trackers and fingerprinting resources, but their weakness, as the paper points out, is that they are not fully exhaustive. New resources are continually being developed and deployed, so these filter lists have to actively play a game of Whac-A-Mole to keep up. However, a countermeasure not discussed in the paper is using tools like Brave Shields, uBlock Origin, or NoScript to fully block JavaScript, since DrawnApart relies on JavaScript.
We tested the three different demos listed on the
project’s GitHub page in Brave and Waterfox with JavaScript blocked by way of Brave Shields and NoScript respectively, and DrawnApart failed to execute. However, it should be noted that blocking JavaScript does not protect against all forms of fingerprinting, as one demo has shown.
The research team disclosed the ongoing results of its study to Intel, ARM, Google, Mozilla, and Brave starting in June of 2020 and continuing through 2021. The
Khronos WebGL Working Group, the developer of WebGL, has responded to the disclosure by convening a technical study group to discuss the results with browser vendors and other stakeholders.