Insidious Android Malware With Russian Ties Eavesdrops On Your Audio, Location And More
The malware, sneakily called “Process Manager” on Android devices, appears as a gear-shaped icon not dissimilar to the settings icon in default flavors of Android. Then, a warning about app permissions is displayed to the user when the app is run, outlining screen lock permissions, storage encryption, and disabling of cameras. After the user accepts these, the icon is hidden, and the app runs in the background. However, this “warning” does not give the full extent of permissions that the app receives, which you can see below.
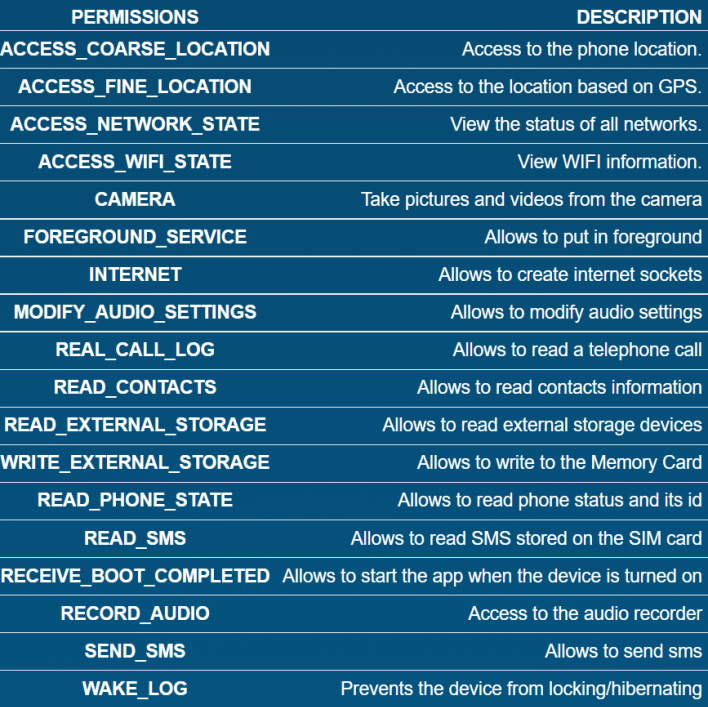
In any event, the Lab52 researchers found that the malicious app first creates a notification channel for “Battery Level Services,” followed by an intent to configure the device with administration permissions. Once the application is configured, functions of the app named after the alphabet are executed to steal information from the device and add it to a JSON file. This data collection includes phone calls, contacts, all device files, location, audio recordings, text messages and other items which, once collected, are shipped off to the command-and-control server identified as being owned by Turla.
Beyond this, the application also tried to download an application called Roz Dhan using a Google-shortened link. While the legitimacy of this app is questionable, it seems that malware abuses it to make money as it has a referral system that likely works when someone downloads the app using a special referral link.

All told, this is an interesting development, but it is not particularly surprising considering Turla is known for using homemade malware for its operations, as reported by MITRE in our research. However, the Lab52 team does not seem to think that attribution to Turla is possible “given its threat capabilities,” though underestimating threat actors is a dangerous game. Either way, this is a rather interesting piece of malware, so let us know what you think in the comments below.
(App and permissions photos courtesy of Lab52)


