Report Claims 100 Million Samsung Galaxy Phones Shipped With A Fatal Security Flaw
The researchers first discovered the security flaw in the Galaxy S9 and reported the vulnerability to Samsung Mobile Security in May 2021. Samsung responded by issuing a patch in August 2021 that applied not only to the S9, but to a whole list of devices including the Galaxy J3 Top, J7 Top, J7 Duo, TabS4, Tab-A-S-Lite, A6 Plus, and A9S. However, before Samsung released this patch, the researchers reported to Samsung in July 2021 that they had discovered the security flaw again in the Galaxy S10, S20, and S21. Samsung pushed out a patch addressing the vulnerability in these additional devices, as well as all devices running Android Pie or later, in October 2021. Fortunately, these patches mean that users shouldn’t have to worry about attackers exploiting this security flaw, so long as they have kept up with software updates.
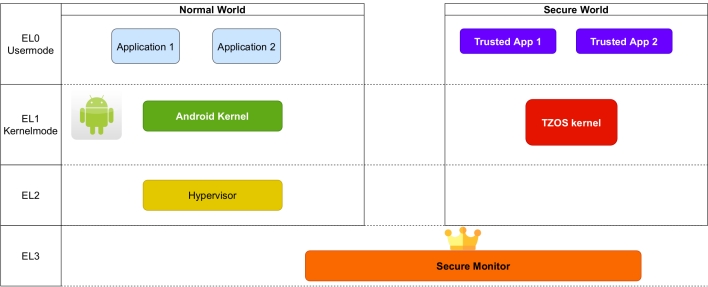
The researchers discovered a difference in the way encryption is handled in Secure World between the Galaxy S8 and devices that came after. The devices make use of the AES-GCM encryption algorithm, which calls for the use of a Number Used Once (nonce). A nonce introduces random noise during encryption, so that no two files, even if they contain the exact same information, appear the same once encrypted.
However, starting with the Galaxy S9, Samsung’s code did not enforce the nonce requirement and even allowed apps running in Normal World to influence or even choose the nonces used. The researchers were able to reuse the same nonce as many times as they wanted and exploit this capability to extract cryptographic secrets inside Secure World. While the Galaxy S10, S20, and S21 contained different code than the flawed code in the S9, the researchers were able to perform an attack that downgraded these devices to the old security protocol on the S9, introducing the same security flaw found on that device.
You can read the full paper for additional details.

