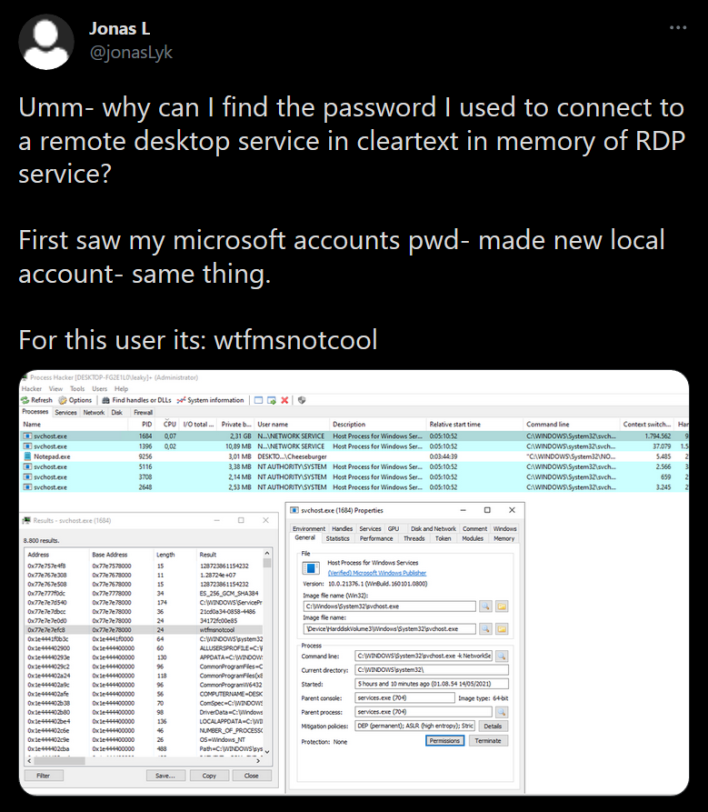
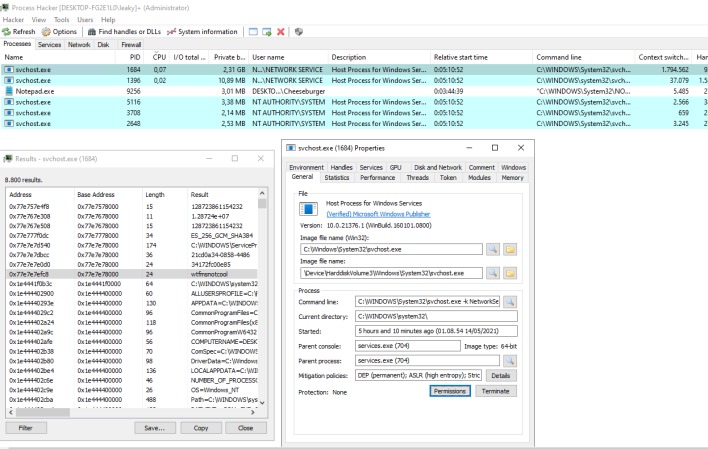
The Remote Desktop Protocol (RDP) is an incredibly useful feature used by likely millions of people every day. Considering it is free and preinstalled from
Microsoft, it beats out most other
Windows-based remote desktop software with ease. This, however, does not give it a free pass from having flaws; however, as a security researcher has discovered his password in cleartext within the RDP service’s memory.
Researcher Jonas Lykkegård of the Secret Club, a group of
hackers, seems to stumble across interesting things from time to time. He recently posted to Twitter about finding a password in cleartext in memory after using the RDP service. It seems he could not believe what he had found, as he tested it again and produced the same results using a new local account.
In the replies, several people could
replicate these results, but it is currently unknown what exact versions of Windows this affects. Before people panic, however, it is not odd for the password to be in memory temporarily, aside from the fact that it is in cleartext. However, what is strange is that it was not properly freed and removed. Of course, this isn't necessarily a reason to panic, but this vulnerability could easily be used for malicious purposes, should an attacker get access to a system.
Having an attacker with remote or hands-on access to a system is quite a few hoops to jump through, but obviously it's not out of the realm of possibility. Therefore, this flaw needs to be fixed as soon as possible to prevent further
security issues from cropping up. As this situation develops, we will hopefully learn more from both Microsoft and Lykkegård, so stay tuned to
HotHardware for updates.