Alarming Phishing Campaign Sneaks Past MFA Security To Carry Out Financial Fraud
Now Microsoft has published details regarding a sophisticated phishing campaign with the ability to bypass multi-factor authentication (MFA). Many phishing attacks send unsuspecting victims to a login page that mimics a legitimate and trustworthy website, but that actually has no connection to the legitimate site and instead simply steals user credentials. The attacker can later use these credentials to login to the victims’ accounts. MFA methods like time-based one-time passwords (TOTP) can help prevent these sorts of phishing attacks from succeeding by requiring that users must enter a time-sensitive code in order to complete the login process. In the case of TOTP, the required code is valid within only a thirty second window, rendering phishing attacks that harvest user credentials for later use ineffective.
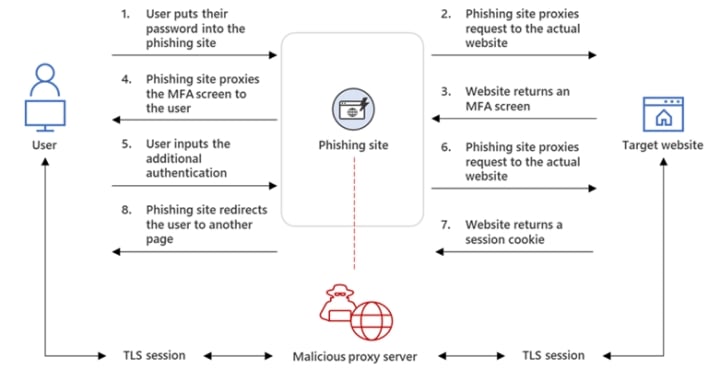
If the user credentials are valid and MFA is enabled, then the legitimate website returns an MFA prompt, which the malicious server proxies back to the user. Upon completing the required MFA step, the phishing site passes the authentication information on to the legitimate website, which issues a session cookie that would normally verify the user’s ongoing authenticated session. However, since the cookie was issued to the malicious server, the attacker gains an authenticated session, rather than the victim.
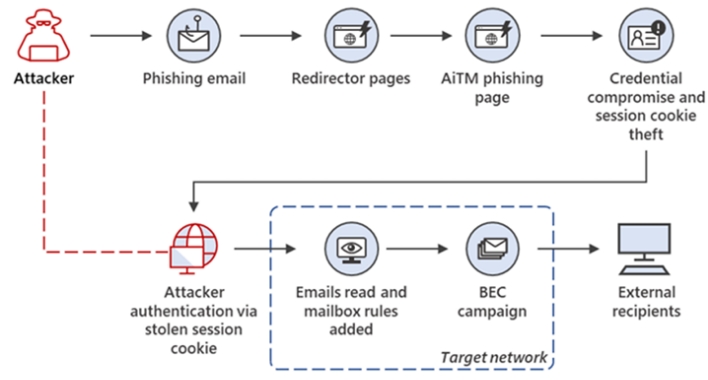
The phishing campaign targets Outlook email accounts, enabling the attacker to access victims’ financial emails with the purpose of finding ongoing email threads. If such a thread is present, the attacker tries to convince the victim’s correspondents to send funds to accounts controlled by the attacker. Microsoft also found that the attacker deletes the original phishing email to remove a sign of compromise and sets up inbox rules that hide the attacker’s correspondence with financial fraud targets.
This phishing campaign’s ability to bypass MFA measures is alarming, but Microsoft emphasizes that the campaign isn’t leveraging any kind of vulnerability in MFA itself. “[S]ince AiTM phishing steals the session cookie, the attacker gets authenticated to a session on the user’s behalf, regardless of the sign-in method the latter uses.” MFA still increases security; it simply doesn’t protect against this particular kind of attack.

