Microsoft Warns Of Toll Fraud Malware Scamming Android Users And Draining Wallets
SMSFactory isn’t the only malware that conducts this kind of fraud. SMSFactory has so far been found in malicious apps that must be side-loaded onto Android phones. However, bad actors have managed to sneak malicious apps bearing the Joker malware family into the Google Play Store time and time again since its first appearance in 2017. Among other malicious activities, Joker subscribes its victims to paid services via SMS.
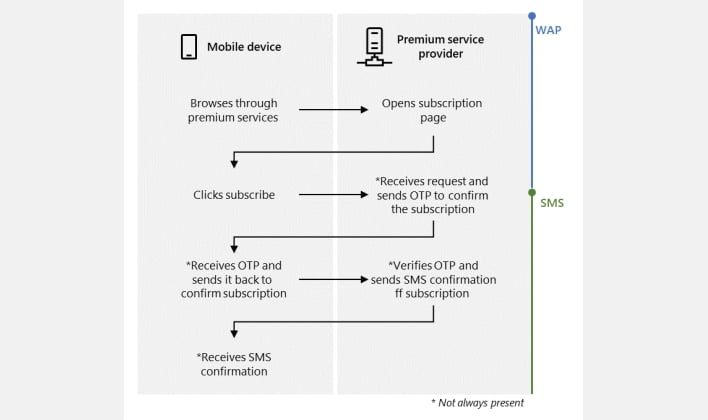
According to Microsoft, the malware attack chain usually begins with the malware either disabling the Wi-Fi connection or waiting for the user to switch from Wi-Fi to mobile data. Once the infected phone is connected to a mobile network, the malware navigates to a premium service subscription page, and injects javascript into the page that clicks the subscription button. If the WAP OTP safeguard applies, then the malware intercepts the OTP that’s sent over text, sends the OTP to the service provider, and finishes by canceling the SMS notifications that might alert the victim to the unauthorized premium subscription.
This automated subscription process is a pretty devilish way to commit fraud, but Microsoft has some suggestions for avoiding the malware that carries out this fraud. The company’s 365 Defender Research Team recommends that users stick to installing apps from the Google Play Store or other trusted sources and avoid giving apps SMS permissions, notification listener access, or accessibility access without understanding why the apps need these permissions. The team also suggests using a trusted anti-virus solution and retiring phones that are no longer receiving updates.

