LockBit Ransomware Gang Allegedly Threatens Murder Of Forum Admin
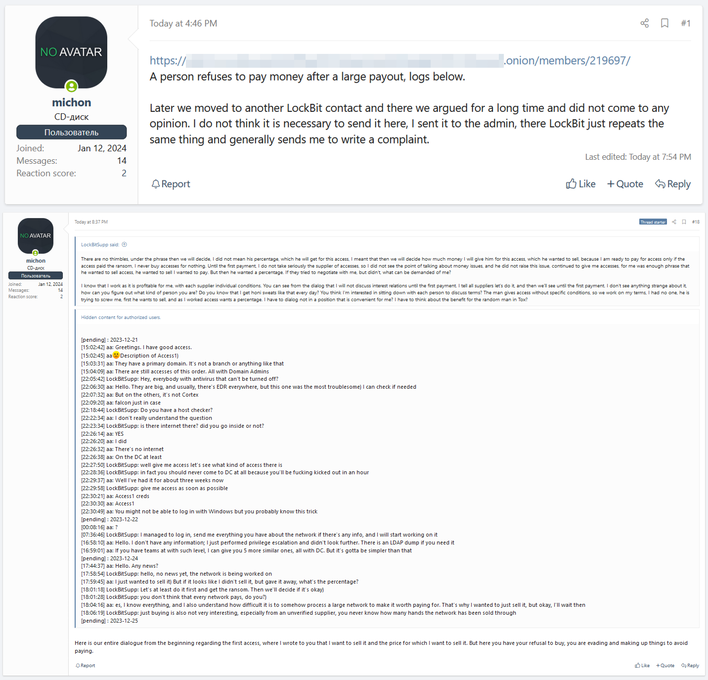
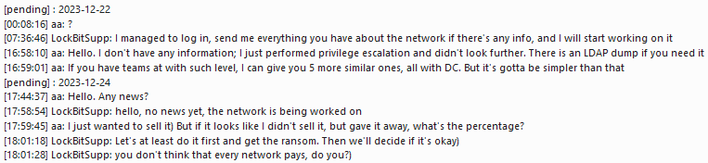
Toward the end of December, the LockBit ransomware group, behind breaches such as those at TSMC, was engaged in chats with another threat actor with a screen name of “aa” or potentially, and hereafter, Michon on hacking forums. Michon was seemingly looking to sell deep access they had gained to an organization for LockBit to ransom or do whatever else with. However, LockBit requested access to check and see what kind of access there was, which Michon granted so that the group could begin working on the network. Over the next couple of days, it could be assumed that LockBit leveraged this initial access to begin to steal data and deploy ransomware on the network.
On December 24th, Michon reached out asking if there had been any updates on the network, to which LockBit replied that there had not been any news. This was then followed with a note that Michon just wanted to sell the access but that it was becoming clear to them that they had just given it away. As such, they requested what their percentage of the payout would be if a ransom were to come through on it. LockBit responded to this, effectively giving Michon the runaround and explaining the difficulties of the ransomware industry, which you can see in the chat logs above.
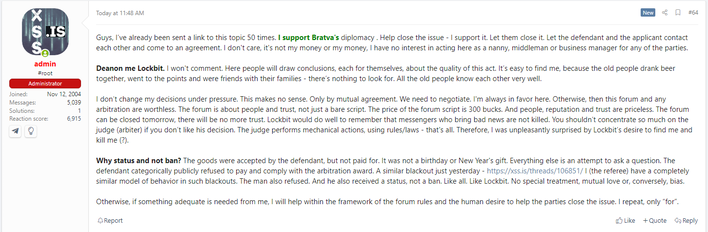
Following this, Michon posted these chat logs and some other details, all of which were shared by @3xp0rtblog on X, to a popular hacking forum to expose the group for what would appear to be a scam. While this should come as no surprise in the criminal underworld, the community reportedly backed Michon in the claim against LockBit. Subsequently, LockBit was banned from both this hacking forum and, evidently, several others around the internet. However, the debauchery does not end with just a simple forum ban.
On January 6th, @vxunderground on X stumbled upon a post from the popular hacking forum’s administration about the incident. This post can be summarized with the explanation that even though this is a criminal world, there are still rules, and honor among thieves must be respected so to speak. This post also indicates that there had been an escalation in the ordeal, with a purported desire from LockBit to find and kill the administrator. With this, the vx-underground team spoke with Lockbit and found that the “Lockbit administration staff said they never explicitly stated they wanted the [forum] administrator murdered - they said they will do as they deem fit when they get his personal information.”
Regardless of the intentions, this is a clear, unprecedented escalation in the ransomware world. It also raises questions about the current status of LockBit and whether the group is looking to exit the ransomware business or adjust its model. We saw similar activity in 2022, when the Conti group used a pseudo-war with Costa Rica to orchestrate its own demise, go offline and restructure. This may be happening with LockBit now, but we will have to continue watching to see what happens, so stay tuned to HotHardware for the next episode of what feels like a telenovela in the ransomware underworld.