Intel Advances Chip Design To Thwart Future Spectre-Style Speculative Execution Attacks
Transient execution vulnerabilities are “a class of vulnerabilities that can allow an attacker to infer information that would otherwise be prohibited by architectural access control schemes.” As Intel explains, an attack using these vulnerabilities would exploit mis-predicted transient instructions created and squashed by speculative execution. The data in these transient instructions could be observed and extracted via secret channels within or across hardware protection domains, referred to as domains in this context.
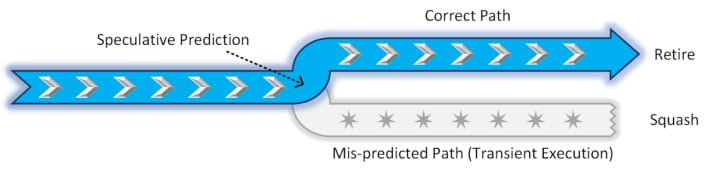

While the simple and perhaps obvious solution would be to stop speculative execution altogether, this could have massive ramifications. CPU architecture improvements over the years, including speculative execution, now powers “the internet and everything we do” at a performance level that we have come to expect. Moreover, this is a new field of research, and these attacks are quite complex and hard to enact outside of a lab setting. However, Intel is committed to “design hardware, firmware and software that collaborate across all elements of the stack,” so transient execution vulnerabilities become fewer and far between.
Over time, Intel has “been able to implement mitigations that allow for safer and more efficient execution,” while still tackling known vulnerabilities. However, this is not the only necessary thing, as “defensive coding practices are a best practice that decrease exposure to a variety of weaknesses,” among other defenses.
With all of this in mind, Intel believes that with an “unparalleled scope of hardware, firmware and software expertise,” the company is “uniquely positioned to deliver protective technologies that continue to support our customers’ success.” We will have to see if that truly holds up in the future, so stay tuned to HotHardware as we have reached out to experts in the field for comment.


