GeForce RTX 5090 Can Smoke An 8-Digit Password In Just A Few Hours
Hive Systems used only 12 RTX 5090 cards for this experiment. You might be cocking your eye at "only", but remember that even at $4k a pop, a set of twelve cards would amount to around $48,000; make it $60,000 with the accompanying infrastructure. That amount may be a serious chunk of change for a mere gamer, but it's nothing for a seriously invested cracker, especially one backed by criminal or government money.
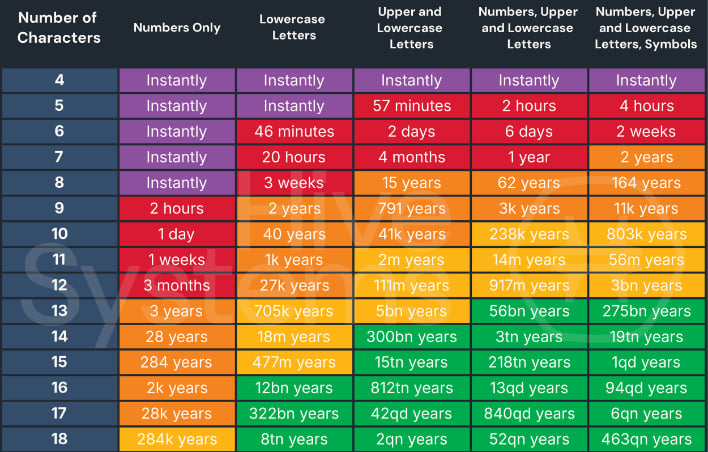
The first takeaway from this table is that the best defense against your password being dug up is still to increase its length. Using a password manager helps a lot with that, especially if you use the pass-phrase variation, i.e. "correct-horse-battery-staple". Using passkeys is also a recommended alternative, as they ditch passwords entirely and thus avoid the common human pitfall of creating passwords that are short, easy to guess, or both.
Even if you do use a password manager, it's very important to be mindful of the length of your master password. As Hive Systems notes, LastPass was hacked not even three years ago, and it's possible that some of its passwords have already been cracked, thanks to LastPass's default setting for iterations (rounds of hashing) being just 5,000. That number seems high for a high-grade hash like PBKDF2 SHA256, but it's not that impressive in the face of server GPU setups becoming many orders of magnitude faster in just a few years thanks to the AI craze.
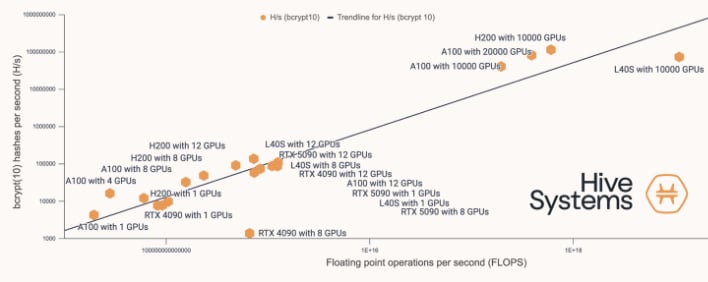
While we're on that topic, Hive System's team also produced estimates of how long it'd take for the horsepower that backs ChatGPT to crack passwords in the same manner as its test, and the results aren't pretty. Even an eight-character random password mixing numbers, lower and uppercase characters, and symbols can be busted in just 2 months. Having recently used some password recovery software myself, I can tell you it's absolutely mind-boggling how many combinations per second even a low-end consumer GPU can process.
Additionally, remember that all of these calculations are for crackers finding random unique passwords. If your password is short and uses common dictionary words, or if it's been reused in a hacked site, then it'll be instantly calculated thanks to common dictionary attacks and rainbow tables. The website HaveIBeenPwned is an excellent resource; enter your email there and it'll tell you which account(s) using that email were part of past data leaks. While we're on recommendations, I'm a big fan of BitWarden, a free and otherwise very cheap password manager with open-source clients for multiple operating systems, and the option to host data yourself.
By the way, here's a message for the Hive Systems folks -- disabling F12 and right-click on your website doesn't increase its security or prevent anyone looking at the source code. Thought you should know.

