FBI Security Advisory Reveals Blackcat Ransomware Gang Clawed $300M From Victims
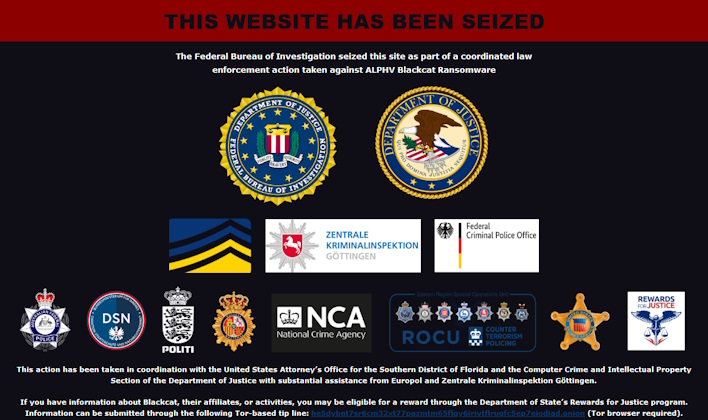
Yesterday, the Justice Department and FBI announced a “disruption campaign” against BlackCat or ALPHV. This campaign enabled the FBI to access the BlackCat ransomware group’s network and infrastructure, allowing the seizure of several of the group’s websites. Further, the FBI was able to publish a decryption tool that allowed over 500 victims from around the world to restore their systems and data, while avoiding paying ransom.
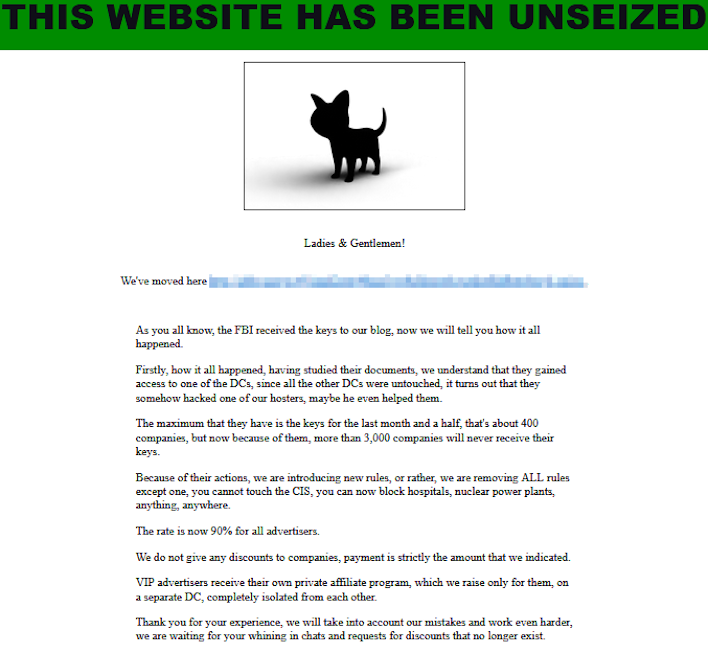
The announcement also notes that “The disruptions caused by the ransomware variant have affected U.S. critical infrastructure – including government facilities, emergency services, defense industrial base companies, critical manufacturing, and healthcare and public health facilities – as well as other corporations, government entities, and schools.” This is particularly interesting as following the announcement, BlackCat/ALPHV “unseized” its domain, announcing that due to the FBI’s actions, 3,000 organizations would not receive decryption keys.
Moreover, this announcement states that the group is removing all rules on attacks, save for one regarding not attacking the Commonwealth of Independent States, which includes states in Russia’s sphere of influence. This, in theory, allows the group to “block hospitals, nuclear power plants, anything, anywhere,” if the group was not doing that already. Finally, this ransomware gang also has changed its ransom split percentage to 90/10, meaning that with the increased risk in associating with the group, partners would gain more reward.
In any event, CISA and the FBI have also released a joint cybersecurity advisory outlining BlackCat/ALPHV’s tactics, techniques, procedures (TTPs), and indicators of compromise, which ought to aid administrators in defending against this threat. The advisory also explains that the ransomware group has targeted over 1000 victims worldwide, demanding $500 million, while receiving $300 million thus far. This indicates that BlackCat is a fairly dangerous threat. The question is, once the group is gone, will it leave a position in the ransomware that another group can usurp? Only time will tell, so stay tuned to HotHardware for the latest regarding the takedown of ransomware gangs.