DarkGate Exploit Targets Full Control Of Unpatched Windows PCs So Update ASAP
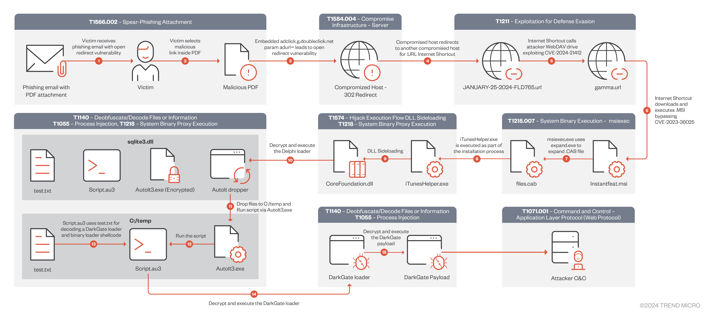
The infection chain begins with a victim receiving a phishing email using an open redirect, meaning clicking a link could send you elsewhere besides that link, in this case, a compromised web server. This web server hosts a .URL internet shortcut file that exploits CVE-2024-21412 by redirecting to another internet shortcut file, which itself points to an attacker-controlled WebDAV server hosting a .MSI file containing a zip archive that can exploit CVE-2023-36025, a vulnerability that allows the bypass of Windows SmartScreen.
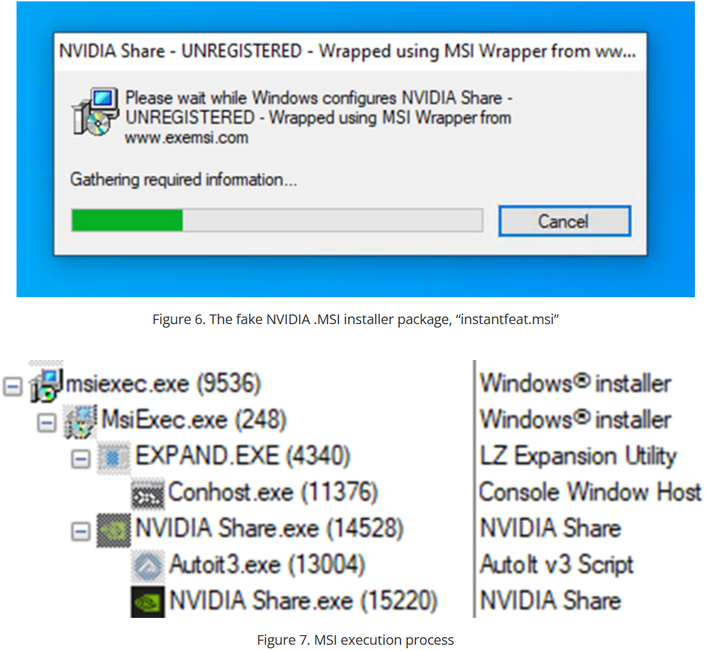
When this package is run, it runs as if it were installing something and sideloads a DLL file containing the malicious installation logic. This DLL drops a compressed file in a temporary directory, which is then decompressed using the Windows tool expand.exe. This decompressed file contains a legitimate piece of software, such as NVIDIA Share, in the example shown in the research. This legitimate is then used to sideload a trojanized version of libcef.dll, which runs automated executables and scripts to establish the DarkGate malware.
Researchers from TrendMicro who reported on this explained in the deep dive of the DarkGate malware that it has existed as malware-as-a-service on Russian-language hacking forums since 2018. Its capabilities include “process injection, the download and execution file, information stealing, shell command execution, keylogging abilities,” which means it is robust.
Thankfully, the core vulnerability behind all this, CVE-2024-21412, was patched in the February 13th security update for Windows. Therefore, if you are not yet patched, you should definitely look to be soon, as threat actors are using the now-fixed vulnerabilities for their gain. Regardless, keeping up with the latest security patches is just good cybersecurity hygiene, so you should be doing that anyway.