Control Web Panel Security Exploit Leaves 200K Linux Servers Vulnerable To Remote Hacks
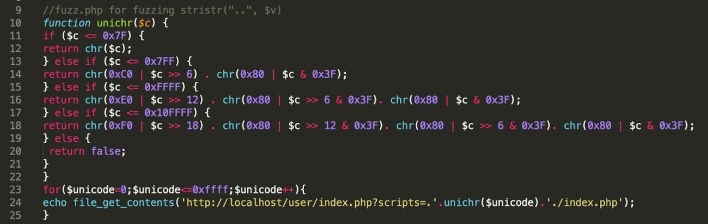
Ethiopian security consulting service Octagon Networks found a flaw in CWP that is about as bad as it gets: remote code execution without authentication. That means anyone who can issue requests to your server can gain full remote code execution. This is, obviously, quite serious, so you can pause reading to go patch if you need to (and then go clean out your underpants.)
Combining that "file inclusion" flaw with another "file write" vulnerability, an attacker can basically modify any file on the system, and given that ability, means that they can pretty much pwn the whole box remotely. It's basically just as bad as the Log4shell vulnerability found in Log4j back at the end of 2021, although that vulnerability affected hundreds of applications due to the widespread nature of that tool.
CWP may not be as ubiquitous as Log4j, but it's still quite common. Octagon's own research claims there were some 200,000 vulnerable servers at the time of its discovery, although BleepingComputer puts the number closer to 30,000. In either case, this is still a major vulnerability. In a bit of dark comedy, when Octagon first revealed the flaw to CWP's developers, they pushed out a simple one-line patch that did absolutely nothing to mitigate the flaw.
There's now a more proper fix out, though. The specific CVEs are CVE-2021-45467 for the file inclusion flaw, and CVE-2021-45466 for the file write vulnerability. To date Octagon has not released full example code for the exploits as there are still many vulnerable servers, but you can hit up the company's blog to read its more in-depth summary of the attack.