Alarming ASUS Armoury Crate Vulnerability Can Give Hackers Admin Access
The ASUS Armoury Crate software was designed to help users control and customize system settings like RGB lighting, fan speeds, and system configurations on ASUS PCs. However, the As103.sys functionality of the software has a flaw that could allow hackers to bypass authorization and gain direct access.
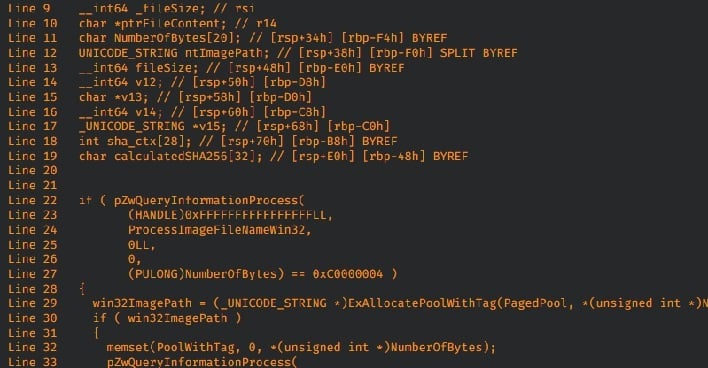
However, to exploit this vulnerability, an attacker must already have some form of access to the system, usually through methods such as phishing, malware infection, or a compromised low-permission account.
Talos intelligence published a full report on this security flaw. ASUS recommends updating your Armory Crate installation to the latest version to reduce your chances of falling victim to a successful exploit. You can do this under Settings > Update Center > Check For Updates > Update.

