Massive Security Flaw ‘Heartbleed’ Exposes Yahoo Mail And Internet HTTPS Encryption
Terrible news, everyone: There’s a coding error in the OpenSSL cryptographic software library that allows anyone with the right tools and a little know-how to access secret encryption keys, usernames, passwords, and even content on sites using OpenSSL for protection. That includes roughly two-thirds of the Internet’s web servers, according to Ars Technica.
The problem with the so-called Heartbleed bug is that there’s a missing bounds check. “By abusing this mechanism, an attacker can request that a running TLS server hand over a relatively large slice (up to 64KB) of its private memory space,” wrote cryptographer Matthew Green in a blog post. “Since this is the same memory space where OpenSSL also stores the server's private key material, an attacker can potentially obtain (a) long-term server private keys, (b) TLS session keys, (c) confidential data like passwords, (d) session ticket keys.”
What’s frustratingly pernicious about this particular exploit is that even though a fix is relatively easy--you just need the server updated to OpenSSL 1.0.1g--but if your server has been accessed via the bug, you need to get a whole new certificate, regardless whether you’ve patched it. But there’s no way of knowing whether or not a server has been accessed in this way, so the nuclear option as it were is the only way to be completely safe.
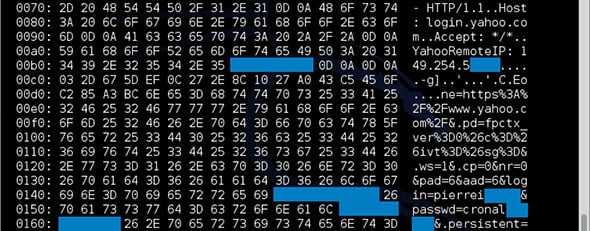
For an example of how dangerous this all is, consider the case of Yahoo. Malware analyst Mark Loman ran a test that determined Yahoo was vulnerable to the exploit. Yahoo is the largest email provider in the world, and every single Yahoo user was potentially affected.
Yahoo since tweeted that “Our team has fixed the #Heartbleed vulnerability across our main properties & is implementing the fix across our entire platform now” but otherwise has not provided any guidance on what users should do to be safe.
The problem with the so-called Heartbleed bug is that there’s a missing bounds check. “By abusing this mechanism, an attacker can request that a running TLS server hand over a relatively large slice (up to 64KB) of its private memory space,” wrote cryptographer Matthew Green in a blog post. “Since this is the same memory space where OpenSSL also stores the server's private key material, an attacker can potentially obtain (a) long-term server private keys, (b) TLS session keys, (c) confidential data like passwords, (d) session ticket keys.”
What’s frustratingly pernicious about this particular exploit is that even though a fix is relatively easy--you just need the server updated to OpenSSL 1.0.1g--but if your server has been accessed via the bug, you need to get a whole new certificate, regardless whether you’ve patched it. But there’s no way of knowing whether or not a server has been accessed in this way, so the nuclear option as it were is the only way to be completely safe.
For an example of how dangerous this all is, consider the case of Yahoo. Malware analyst Mark Loman ran a test that determined Yahoo was vulnerable to the exploit. Yahoo is the largest email provider in the world, and every single Yahoo user was potentially affected.
Yahoo since tweeted that “Our team has fixed the #Heartbleed vulnerability across our main properties & is implementing the fix across our entire platform now” but otherwise has not provided any guidance on what users should do to be safe.