TeaBot Malware Taints Google Play Store Again, Now Targets US In This QR Scanner App
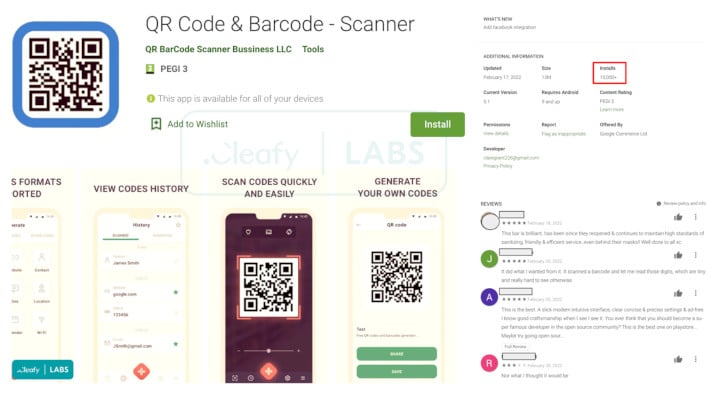
Image Source: Cleafy
This Add-On version of the app doesn't do anything beneficial at all. However, what it does is ask for permission rights to Android's accessibility services. The problem here is that the accessibility services permission is almost super-user-like when it comes to permissions on Android, and while Android 12 does have fixes in place for this, most Android devices still run Android 11 or even older. So when granting accessibility access, it also allows the app to grant itself permissions to other features without user knowledge, such as screen capture, text message content, and more. That makes the malware, named TeaBot, particularly effective as a tool for stealing banking, crypto exchange, and other financial login information.
This particular instance of TeaBot is not quite the same one that has existed for months now. In January, there were reports of apps that included or distributed the malware, that Google already flushed from the Play Store. Those first versions primarily targeted people in European countries, with code specifically telling it not to run if the user was in the US. However, this new version has added code to make sure it does run on US users now. Though the early instances of the malware have already been cleaned off the Google Play Store, the difficulty in keeping up with it stems from the fact that malware distributors are getting more sophisticated. Notably, they utilize what is known as a "dropper" method.
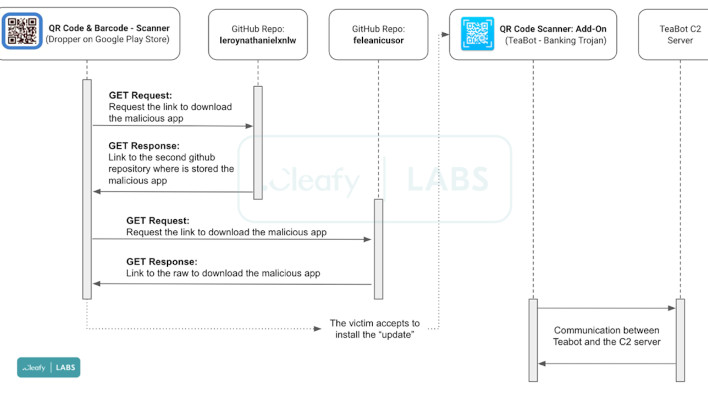
Image Source: Cleafy
A dropper is a method of delivering malware that allows real app installations without worrying about scanners or checks from deployment staff. That app then gets the malware from some other server or service. That means that until the app performs its actions to get the malware it can not be flagged as a malware-laced app. Additionally, in this case, the app in question is a real working app and would not be flagged by anti-malware software. Malware preventative software would only flag this app, so the original software would remain, giving it another chance to download its nefarious payload again.
Of course, this is not the only instance of a dropper being used in malware distribution. Recently there was a report of the dropper method being used in Windows Store Apps. The biggest problem here is that the originating app is legitimate, thus giving it positive reviews, making it seem trustworthy when it is not. So the best course of action is preventative. First, double-check you don't already have a QR code scanner installed. Also, be aware that iPhones and most Android phones already have a QR code scanner, so there is no need to install any new app. Monitor any network using activity from your apps and pay attention if you see an app installed you don't remember doing yourself. Lastly, keep your number of installed apps to a minimum of just what you need anyway, because too many apps can slow down your mobile computing experience.

