Security Report Blows The Whistle On A Massive Android TV Botnet Campaign
This week, researchers out of Qianxin Xlabs, a Chinese research group, published a report on the threat group Bigpanzi. This discovery began with the finding of a virus sample called pandoraspear, which contained nine hardcoded C2 domain names. Two of these domain names were expired, so the researchers elected to register the domains and determine the botnet's size. This allowed them to find that the network had 170,000 daily active bots which are primarily based out of Brazil.
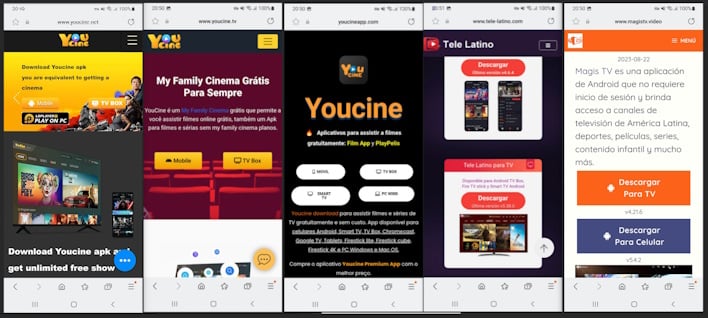
While the Bigpanzi gang went after the researchers after they made this discovery, the investigation continued. This allowed them to find several download scripts and other information, further revealing the threat actor group’s infrastructure and motives. Namely, it is noted that the group “primarily targets Android OS TVs and set-top boxes, as well as eCos OS set-top boxes.” This is based on getting users to install apps or updates to gain control of the systems rather than relying on leveraging vulnerabilities.
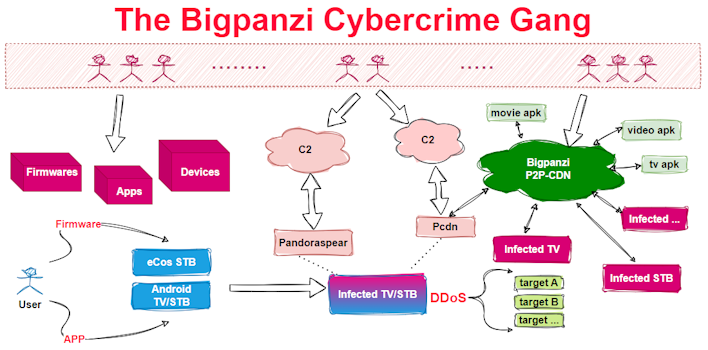
How this group operates and its potential capabilities are rather interesting, as this is something that has yet to be seen. Further, it is fascinating that they have been able to lay low for so long without discovery while being so widespread. You can see the full coverage of the group on the Xlabs site, but perhaps the key takeaway is that one should not just install apps to devices willy-nilly without knowing where they come from.


