Massive 47GB Data Breach Exposes Millions Of Passwords For Google, Netflix And More
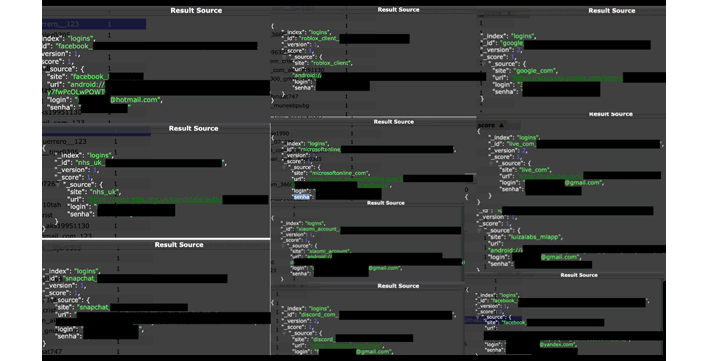
Fowler says that the database held "login and password credentials for a wide range of services, applications, and accounts, including email providers, Microsoft products, Facebook, Instagram, Snapchat, Roblox, and many more." Perhaps more concerning is that he also claims to have seen login details for "bank and financial accounts, health platforms, and government portals from numerous countries," which means that this data likely wasn't collected through phishing or similar means.
Instead, Fowler posits that this database, while potentially legitimate and accidentally exposed, was more likely built using a type of malware known as an infostealer for reasons that are likely obvious from the name alone. Infostealers, like RedLine or Raccoon Stealer, most commonly target browser profile information such as autofill information, which is often poorly encrypted and quite valuable. Session cookies are another common target, as they're even easier to exploit.

The best option would be to use a password manager. Services like 1Password, Bitwarden, and NordPass can allow you to use a strong, memorable passphrase with multi-factor authentication (including physical security keys like YubiKey, or biometrics) to consolidate many accounts into one service that offers strong encryption and a zero-knowledge model, so that even if the password manager is hacked, attackers still can't get at your master password.
Fowler unfortunately didn't retain a copy of the database due to personal legal liability concerns, so we don't know exactly who may have been affected. However, it's a good idea to bookmark the website "Have I Been Pwned" which lets you put in your e-mail address and see what breaches included it. If your account has been pwned recently, better change that password.


