Bumbling Iranian Hackers Expose Their Own Cyber-Spy Training Videos Online
ITG18 is an Iranian state-sponsored threat group. They are also referred to as APT35 or Charming Kitten by other security researchers. The group uploaded more than 40 gigabytes of data onto an unprotected server back in May 2020 that was being monitored by the IBM X-Force IRIS. The data included five hours of video footage and some of that included training videos.
The training videos were recorded roughly one day before being uploaded to the server. They illustrated how hackers could quickly access compromised email accounts and exfiltrate datasets with information such as files uploaded to cloud storage, photos, and contacts. They were able to manage multiple email accounts at the same time through collaborative software like Zimbra.
The hackers targeted other kinds of accounts aside from email accounts as well. The researchers noted that the hackers had a document filled with usernames and passwords. These kinds of accounts varied from bank accounts to pizza delivery services. The hackers appeared to also gather “trivial social information” about their victims, but the security researchers did not specify what kind of information or from what sites.
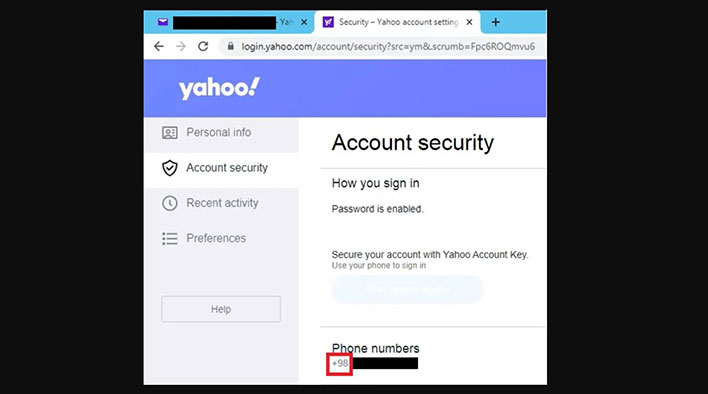
The training videos primarily featured dummy accounts. Some of these dummy accounts were used by the hackers to also send phishing emails and for other purposes. The security researchers were able to gain a better understanding of who the hackers were. For example, one of the dummy accounts revealed the Iranian phone number that was linked to it.
The security researchers were able to uncover some of the hacker’s primary targets from this data. Some of the videos showed the information of real targets instead of dummy accounts. Targets included members of the United States and Greek militaries. The hackers had been able to steal a variety of information from these targets, including tax records. IBM has since notified those whose accounts were compromised.
Interestingly, the hackers were unable to access accounts with multi-factor authentication (MFA). The researchers recommend that people protect themselves by using MFA, periodically resetting their passwords, using a password manager, and being careful with privacy settings and third-party apps. There is no guarantee of protection against hackers, but simple security measures can help.
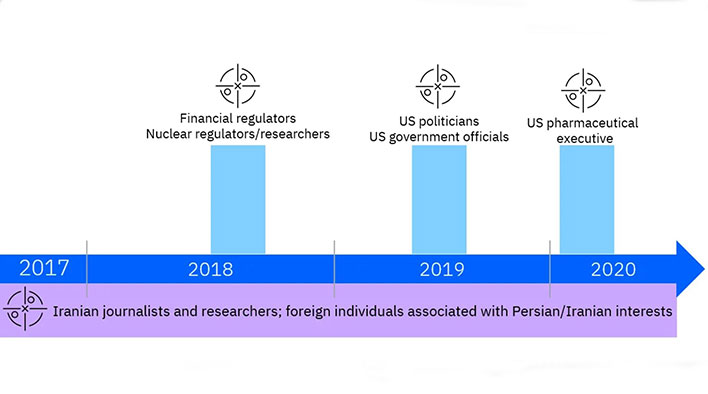
The hackers are currently targeting pharmaceutical companies and the United States presidential election. They have also historically attacked those with Iranian connections. Many of their attacks align with global events like the recent American extension of sanctions against Iran. According to the security researchers, "ITG18 has demonstrated it performs operations to serve multiple, distinct long-term objectives that align to Iranian strategic interests."
It was also revealed that the Russian threat group known as APT29, "The Dukes", and/or "Cozy Bear" is currently targeting institutions that are working on a vaccine for COVID-19. The United Kingdom’s National Cyber Security Centre (NCSC) recently published an advisory about the group’s activity. They also published an assessment that is intended to help institutions protect their networks and data.