Iranian Hacker Group Deploys New Attacks Targeting Nuclear Security Experts
Earlier this year, the Proofpoint Threat Research Team, alongside Senior Threat Researcher Joshua Miller and Senior Reverse Engineer Pim Trouerbach, unraveled the latest in TA453’s reconnaissance operations. It now appears that the group is targeting nuclear security and foreign policy experts, as mentioned, through several new tactics. In short, the group is masquerading as an organization to try and get feedback from the experts on content sent via email.
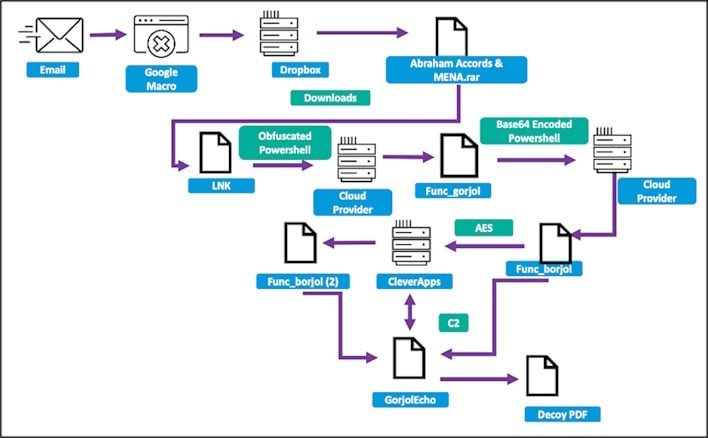
The chain of events started with what appeared to be a benign email to the experts regarding Iran and global security. Of course, this was followed by another email that would deposit a link to a Google Script macro that would redirect to a Dropbox URL containing a RAR file with a dropper called “Ab raham Accords & MENA.pdf.lnk.”
Normally, Charming Kitten would use VBA macros of remote template injection, according to the Proofpoint report, but this has become more advanced. Following the initial access, obfuscated PowerShell from the dropper would call out and pull down a second stage, establishing persistence in a mundane way.
This second stage would also display a decoy PDF matching the content of the email conversation before exfiltrating encrypted information about the infected device. At this point, the threat actors could then control the infected device, though, as it turns out, not everyone has a Windows device.
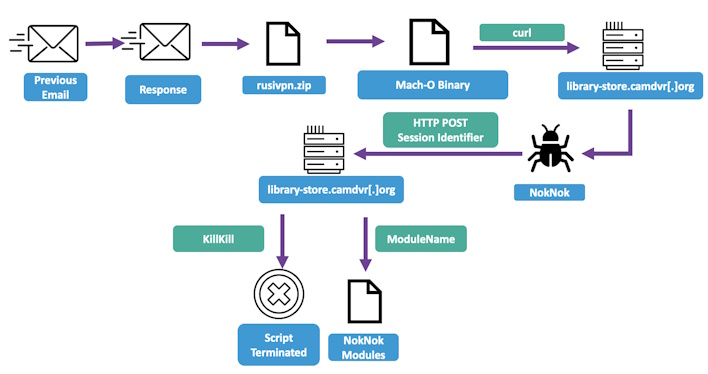
With this new problem, the group adapted and reached out to the victim, who had an Apple device with an updated payload that would work on MacOS. This payload would appear as a VPN solution and share drive GUI application themed around the organization TA453 was masquerading behind. Of course, this would kick off a similar infection chain for the same purposes.
What is most curious about all this is that this new operation comes on the heels of Joint Comprehensive Plan of Action (JCPOA) negotiations, otherwise known as the Iranian nuclear deal, directly involving Tehran. Given this and other evidence, Proofpoint continues to assess that TA453 operates in support of the Islamic Revolutionary Guard Corps (IRGC), specifically the IRGC Intelligence Organization (IRGC-IO).
At the end of the day, as the pressure increases on Tehran, the need for relevant intelligence grows. As such, we could expect increasingly clever techniques to penetrate adversaries or those involved in JCPOA. Hopefully, however, researchers at Proofpoint, among other defensive organizations and agencies, can thwart these highly specialized and targeted attacks for the greater good.