IKEA Under Ongoing Cybersecurity Assault As Criminal Hackers Relentlessly Hammer Its Email System
Reply-chain email attacks occur when a threat actor takes over a legitimate email account and sends an email impersonating that person in an email thread. Typically, these emails will contain files or links to files that have malware embedded in them, so that the attacker can continue to maintain access to the company or access additional assets. This method of attack can be quite effective, as the person receiving the email likely trusts the sender and is, therefore, more likely to download a file or open a link.

In this case, BleepingComputer acquired an email from IKEA support staff explaining that there is a reply-chain attack coming from internal mailboxes as well as from “other compromised IKEA organizations and business partners.” This leaked email further explains to IKEA staff that the reply-chain emails contain links with seven digits at the end and showed an example email from this attack.
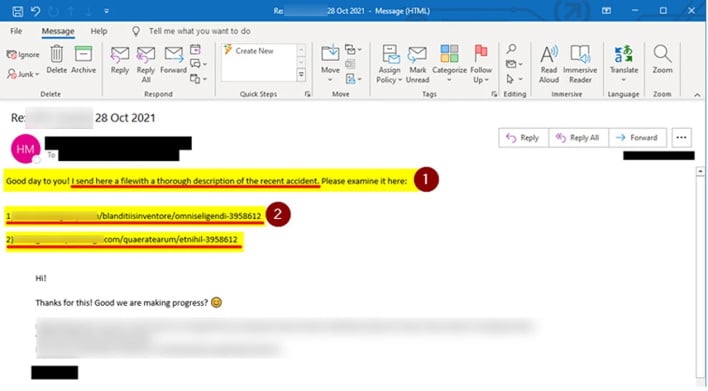
The concerning thing about this attack is that it is unclear if the perpetrators have compromised accounts or have gained access to IKEA’s internal Microsoft Exchange servers. Either way, the emails being sent from trusted accounts have the added concern that unsuspecting users will remove the emails from quarantine, thinking that a mistake was made. As such, IKEA has disabled the ability for users to release emails from quarantine out of an abundance of caution. However, the attackers may have delivered their payloads already, including the Qbot trojan and potentially Emotet, based on VirusTotal submissions found by BleepingComputer.
With these concerns and potential payloads being delivered to its internal networks, IKEA is more than likely on high alert now. In any event, the hope is this will not lead to any further issues such as a ransomware infection, but we will have to wait and see.


