Those GIFs In Microsoft Teams Might Be Funny But Can Also Steal Your Data
Found by Security researcher Bobby Rauch, GIFShell is a rather nasty attack vector in its own right. Previously, Bobby discovered Good Samaritan attacks involving Apple Airtags. GIFShell, however, takes advantage of multiple security flaws in the popular chat and meetings application. The final result of these exploits is that the attacker can gain access to a remote user's shell.
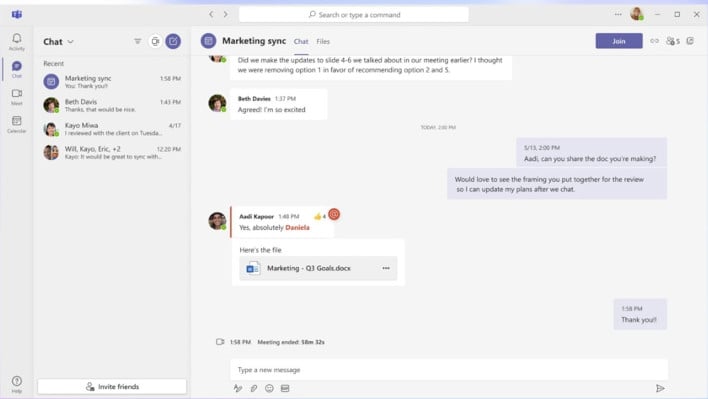
Ultimately, the attack does need at least one user in an organization utilizing Teams to install a stager, but some social engineering work can make short work of that step in the process. Once the stager is installed, the malicious code monitors Teams log files for GIFs. If a base64 GIF is detected, it then decodes the base64 and embeds its own malicious code into it. Next the GIF URL gets rewritten for display, embedding from an attacker's URL. That URL is then disguised as a Teams Card, which shows none of the information about where the GIF is pointing. That Teams card holds data that will be used later.
Short video of GIFShell in Use. Source: Bobby Rauch
At this point in the process, GIFs will auto-load and trigger a web hook confirming to the attacker that the malicious access is available. Next, the attacker needs only to run the commands from their remote shell. This allows for malicious commands to be executed, malicious code to be ran, files to be downloaded, data to be gathered or stolen—all quite nasty.
So, then what is the mitigation for Teams? Well, one major attack vector is Teams allowing for external access settings. Teams Admins can turn this off via the instructions from Microsoft, but some organizations may still need this access. For example, a recruiting organization might need to set up interviews on behalf of their client. In those cases, it's best to use Teams Guest functionality, which is a limited access version of the application. The next mitigation options are to monitor for unusual access to Teams logs files and watch for unusual requests involving the Teams lookup server.
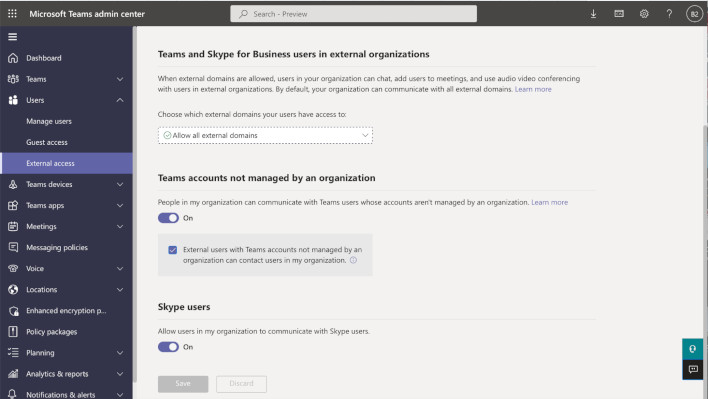
Security settings to change for Admins. Source: Bobby Rauch
Now that this attack vector is public, these dangerous attack vectors can hopefully get patched by Microsoft soon. In the meantime, it is always best practice to be wary of what links you click, and images you load.

