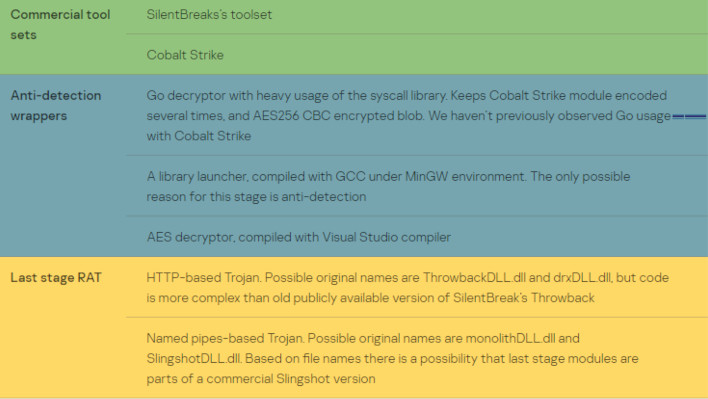
Another day another malware threat. Yes, yet another new way of delivering malware has shown up recently. That new way does not directly involve files but Windows Event Logs.
According to security researchers at Kaspersky, a customer showed this new behavior. The method injects shellcode payloads into the event logs for Windows' Key Management Services (KMS). A custom malware dropper manages to perform this task. The dropper then copies the executable WerFault.exe to a new folder, then places an encrypted binary into that same location. This is the first this method of malware delivery has been observed "in the wild."
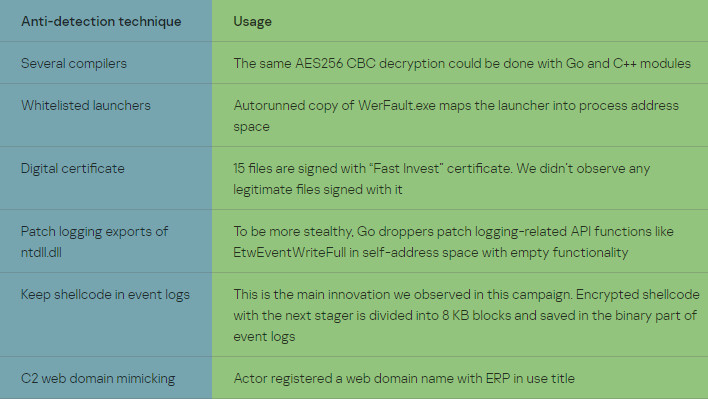
According to Kaspersky's lead security researcher, Denis Legezo, the DLL is basically useless on its own. However, now that the DLL is running, it can be used to execute code in memory, code that it can put together in pieces pulled straight from the Windows Event Log. That is what makes it dangerous.
Many malware and virus detection platforms usually have blocks of code that even heurisitic malware and virus scanners can catch without too much "hard work" by the scanners. However, this particularly nasty version of things can break up all of that code into 8KB chunks, at seemingly arbitrary intervals in the code, store them in events, then re-assemble them later. This means that it's possible for malware detections to just miss them because they could be completely innocuous on their own.
The detection by Kaspersky, they claim, happened in February, and believe that the particular attack they studied was quite targeted. In fact it looks like there were additional anti-malware detection prevention placed into the code. That is in addition to this Windows Event code storage method. They believe the intent of the attack was to steal data, as is quite often the case for malware as of late. We've seen a whole host of banking malware
for mobile devices after all.
When it comes to security of your devices though, it often does boil down heavily to being wary. Be extremely careful of attachments you open, e-mails you accept, and what you install. Kaspersky, nicely,
has published hashes on all files associated in the attack that they detected in their report. It is important to note that, on their own, a number of the files are innocuous and may even be necessary system files.