Critical D-Link Security Flaws Leaves Thousands Of These Storage Devices Vulnerable To Hacks
Roughly two weeks ago, researchers discovered a chain of vulnerabilities in several D-Link NAS devices including “DNS-340L, DNS-320L, DNS-327L, and DNS-325, among others.” The issues live with nas_sharing.cgi, which has a backdoor thanks to hardcoded credentials and command injection through the system parameter. These combined would allow for arbitrary code execution on the afflicted devices, allowing an attacker access to information, denial of service, or otherwise.
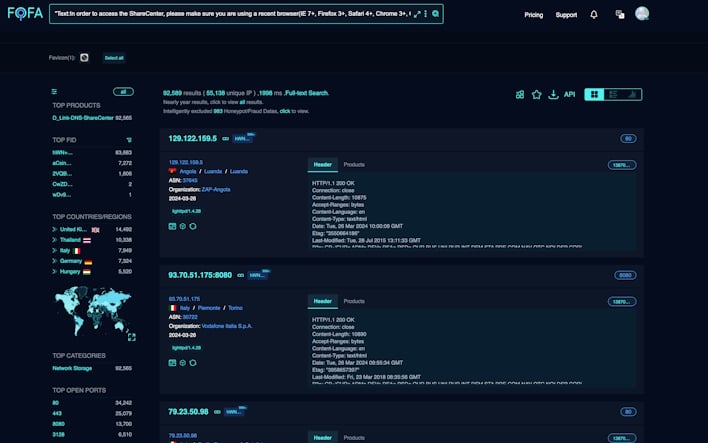
According to the researchers with NetSecFish, up to 92,000 D-Link devices are exposed to the internet and vulnerable to attackers. Shodan shows that there are significantly fewer exposed devices and fewer still that are tagged as end-of-life. Regardless, in response to the vulnerabilities, D-Link posted a notice explaining that the “exploit affects a legacy D-Link products and all hardware revisions, which have reached their End of Life ("EOL")/End of Service Life ("EOS") Life-Cycle.” As such, the recommendation for affected systems is to retire or replace them, as there will not be an update coming from the company.
Of course, you can also always ensure that the NAS devices are not exposed to the internet and simply use them internally, but there's no guarantee that your data is safe. Thus, we would also recommend upgrading your storage server to something more current (16TB Buffalo NAS), to help prevent these types of security issues.


