Shutterfly Issues Statement On Customer Data Following Multi-Prong Ransomware Attack
Earlier this year, three major vulnerabilities, the most severe of which is tracked as CVE-2023-36934, were discovered in MOVEit Transfer, a data transfer software. If exploited, that severe vulnerability could allow an unauthenticated attacker to access the MOVEit Transfer database and recover files. Since its discovery, it has been abused numerous times, especially by groups like Clop, who found Shutterfly was vulnerable.
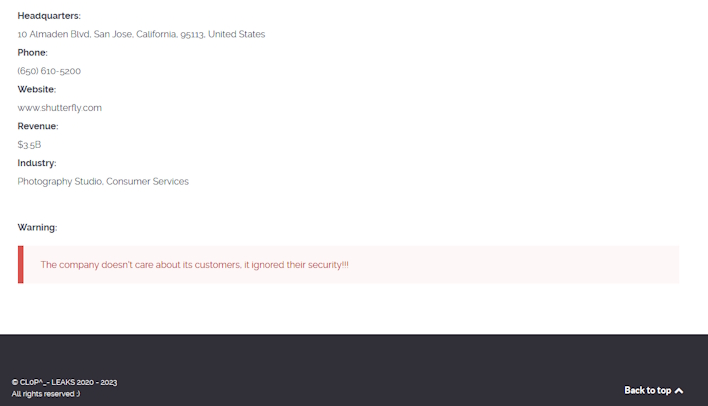
With this, the ransomware group subsequently posted Shutterfly to its website, claiming that “the company doesn’t care about its customers” and “ignored their security.” However, Shutterfly told BleepingComputer that while it was a victim of the MOVEit vulnerability, there was no significant impact affecting either employees or customers. Specifically, the company claims that “After a thorough investigation with the assistance of a leading third-party forensics firm, we have no indication that any Shutterfly.com, Snapfish, Lifetouch nor Spoonflower consumer data nor any employee information was impacted by the MOVEit vulnerability.”
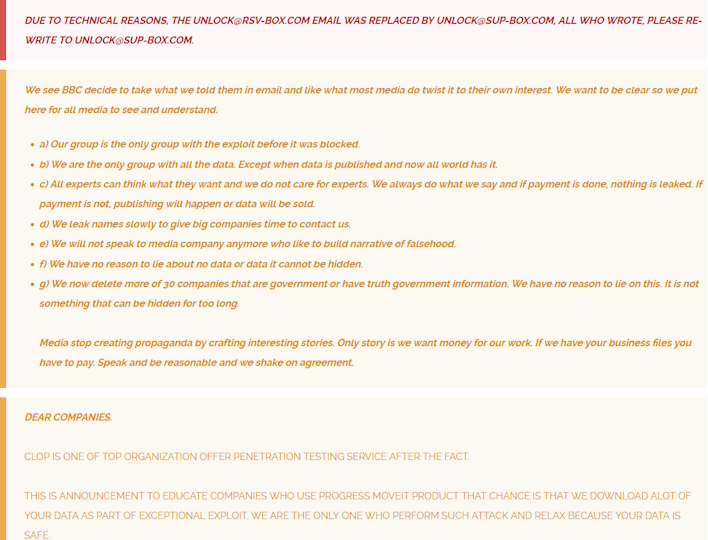
Besides Shutterfly, Clop has also hit companies like Shell, Honeywell, Norton LifeLock, and more. Despite the uptick in hits, though, Clop seems to be struggling some with the new-found infamy. The group’s site is littered with messages about what the group does, like “penetration testing services” for those who used MOVEit products, a tirade about BBC and the group’s ethics, and somewhat funnily, a message about the group’s email being disabled.
Regardless of Clop and its hi-jinks, if you have MOVEit products in your environment, ensuring all your software is up to date would be worthwhile. Otherwise, you might become like any of these other companies that got popped by Clop.


