Call Of Duty Players Caught In Crosshairs Of A Self-Replicating Malware Campaign
Just a few days ago, a thread for Call of Duty: Modern Warfare 2 (2009) popped up in the Steam community, alerting players about needing antivirus before playing. Purportedly, hackers have found a way to replace dsound.dll in hacked lobbies with supposed malware that gets flagged as “Trojan:Win32 Wacatac.B!ml.”
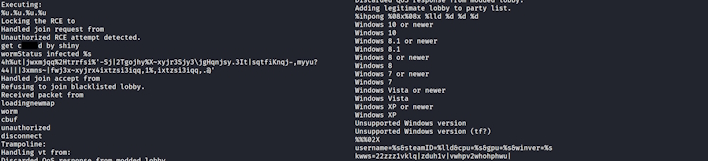
Members of the information security community have begun to dive into this malware just as we have, finding several interesting tidbits of information. First and foremost, this file has many rather questionable strings, including direct references to this malware being a worm. Furthermore, it indicates that the hacker refers to themselves as “shiny.” This name can seemingly be tied back to earlier malware samples that did not have obfuscated code.
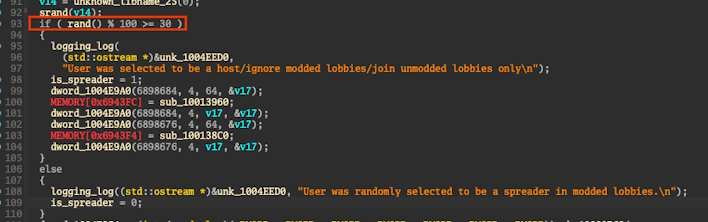
X users @bquintero and @entdark_ noted that with older samples, there is a download of dsound.dll from shinyware[dot]systems and similar worm references. It is also believed that players were selected to be spreaders of the worm with a random number generator. Furthermore, the malware would try and prevent other RCE attempts and potentially even block them.
With this situation ongoing, the multiplayer servers for Call of Duty: Modern Warfare 2 were brought offline to investigate. At this time, though, there have been no updates from the Call of Duty team. Hopefully, whatever vulnerability that is allowing this worm to work will be nipped in the bud soon. As for players who have been playing COD: MW2 (2009), installing or updating your antivirus solution is recommended to help protect yourself, just in case.