Apple Fixes Alarming Spyware Vulnerability On iPhone, iPad, Watch And Mac, Update ASAP
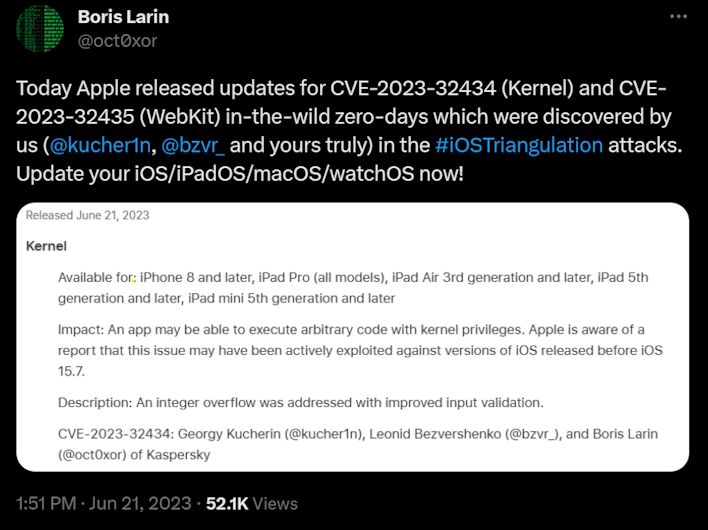
Per Apple Support security content updates, updates for iOS, iPadOS, macOS, and watchOS all contain fixes for the three vulnerabilities that allow TriangleDB to work. The first vulnerability, tracked as CVE-2023-32434, was one of two credited to Kaspersky researchers and is a kernel-level vulnerability that "may have been actively exploited against versions of iOS released before iOS 15.7." The second vulnerability, CVE-2023-32439, is a WebKit problem wherein the maliciously crafted web content could yield arbitrary code execution, which may have been exploited in the wild.
The third and final vulnerability, CVE-2023-32435, is also a WebKit vulnerability credited to the Kaspersky team. Affecting older Apple devices, this vulnerability revolved around the processing of web content that could lead to arbitrary code execution and may have also been exploited in the wild. As Apple published the fixes for these vulnerabilities, Kaspersky published some more insight into what happened with what is called Operation Triangulation.
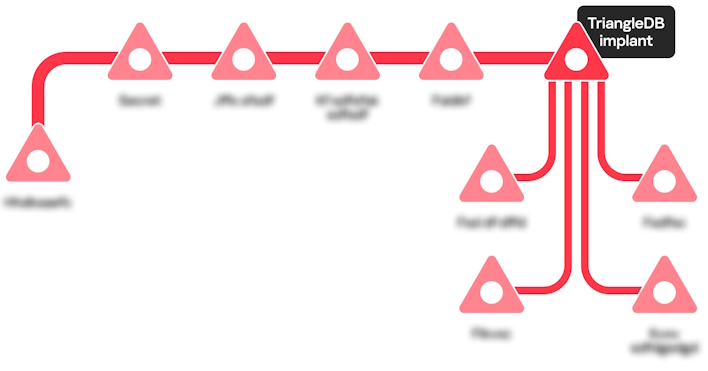
The two vulnerabilities credited to Kaspersky led to the TriangleDB implant at the end of the Operation Triangulation infection chain. This chain is kicked off when a victim receives an iMessage with a malicious attachment that they do not see nor need to interact with, after which attackers gain root privileges on the victim's device. With this access, the attacker then deploys the TriangleDB implant to memory, which means that if a device is restarted, then the implant is lost, and the attack must start again. Provided the device is not restarted, though, the implant will automatically yeet itself after 30 days provided the attackers do not extend the spyware duration.
As far as capabilities go, TriangleDB can interact with the filesystem, including exfiltrating files, interacting with processes, dumping keychain items to get credentials, monitoring the victim's geolocation, and running other malicious modules that also run in memory. All of this was discovered after the Kaspersky Unified Monitoring and Analysis Platform (KUMA) platform discovered "an anomaly in [Kaspersky's] network coming from Apple devices." This turned out to be Triangulation spyware that had infected the iPhones of senior employees at the company.
However, Kaspersky believes that they were not the main target of the cyberattack. It is currently unclear who was to be the main target, but the Kaspersky blog uses the term "worldwide proliferation" concerning the spyware, so technically, anyone is at risk. Therefore, update your devices as soon as you can to protect yourself from the Triangulation spyware.