AMD And Intel CPUs Rocked By New Speculative Execution Attack With A Huge Performance Hit
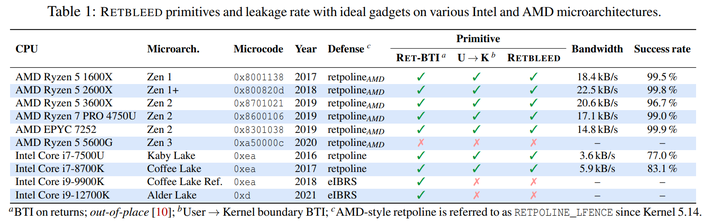
Without getting into the technical weeds, where earlier Spectre attacks targeted indirect calls and jumps, retbleed instead targets returns. It works on both Intel and AMD machines, although it's drastically more effective on the latter. Like earlier Spectre attacks, once executed, it can allow any application executing on the target CPU to read any memory, regardless of whether it has the authority to do so.
Everyone reading this should flip out and rush to patch their systems, right? No, probably not. While retbleed is a very serious vulnerability, it only affects certain hardware: Intel machines from the 6th thru 8th generation Core families, and AMD Zen, Zen+, and Zen 2 systems. Intel says that it's also automatically mitigated by recent versions of Windows, which have Indirect Branch Restricted Speculation (IBRS) enabled by default. IBRS is an effective mitigation against retbleed, so Windows systems are essentially inoculated already.
Linux users on affected machines do have cause for concern, though, and that particularly extends to hosting providers and other folks that allow remote users to login to their systems without supervision. Both AMD and Intel say that they're not aware of anyone making use of these vulnerabilities in the wild, but patches aren't available yet. When they do become available, they may come with a performance hit of as much as 28%. Hopefully some clever coders will come up with a way to mitigate that performance loss.


