Warning! Don't Fall For This Clever Gmail Phishing Scam That Looks Legit
The attack's sophistication lies in hackers' ability to make every element look highly legitimate. In this attack, hackers circumvented the DomainKeys Identified Mail (DKIM) signature checks, which are designed to verify if an email is actually from the acclaimed domain. Due to this bypass, Google will not warn you about an impending cyberattack. In Nick's case, the phishing came from no-reply@accounts.google.com, an email with a legitimate domain. The phishing link, however, has “sites.google.com" in its URL.
How could this be possible? Hackers created an imitation support portal page with sites.google.com, originally designed to help Google account owners create basic websites. A link to the support page is then embedded in the phishing email to trick unsuspecting victims into believing that they are simply interacting with Google. On the support page, victims are then lured into giving away their Google account credentials, which attackers will later use to access their accounts.
It’s worth mentioning that Google could also share the blame for making it possible for anyone to have a site with Google.com appearing in its address in the first place. It's even more concerning that it allows scripts and arbitrary embeds when it knows malicious actors could easily use these features to create credential-harvesting sites. While Google appears to be focused on enhancing users' experience when using their services, the security risk associated with such services seems to outweigh their benefits. Perhaps Google will reconsider its stance regarding it.
Despite the sophistication of the attack, one fact remains true: no matter how legitimate a cyber attack appears, cybercriminals rarely operate without leaving a trace. If you carefully observe a screenshot of the email sent to Nick, as shown below, you'd notice that http://privateemail.com mailed the email, which is a major sign to watch out for, as it makes it crystal clear that the message was not from Google. Nick has provided key points in the Twitter thread below to help you understand the trick behind this attack.
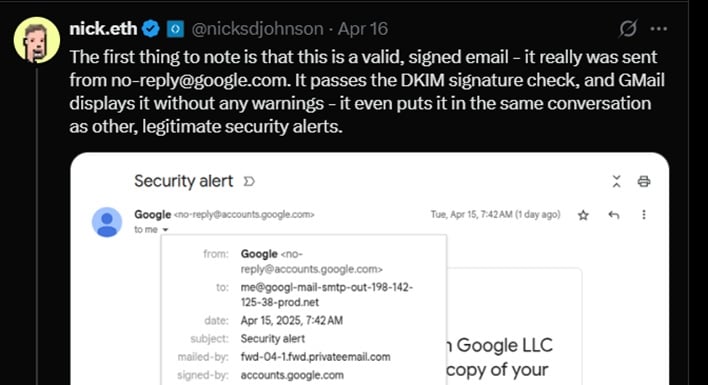
This attack makes it obvious that you can never be too careful when trying to avoid falling victim to the antics of malicious actors. While you can continue inspecting email sender domains and URLS in their emails as a basic security check, you must carefully scrutinize all email addresses involved with a received email. Even after doing this, extra caution is needed, especially when prompted to input your credentials. Hopefully, Google will fix the vulnerabilities exploited in these attacks to prevent further attacks using the same tactics or a modified version of them.

