When it comes to the convergence of convenience and technology,
Bluetooth is right up there with the advent of USB, which is why there are billions of devices that support the wireless standard. Frighteningly, they could all be at risk of more than a dozen vulnerabilities discovered by security researchers Matheus E. Garbelini, Sudipta Chattopadhyay, Vaibhav Bedi, Sumei Sun, and Ernest Kurniawan.
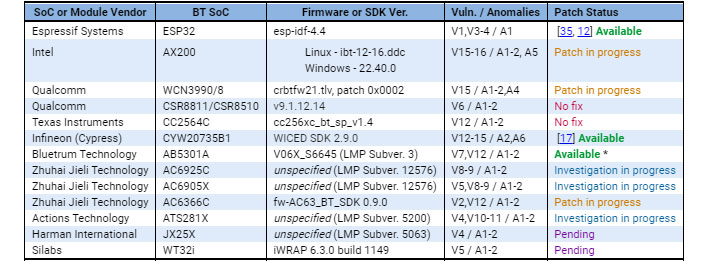
The researchers outlined 16 Bluetooth vulnerabilities found on 13 system-on-chip boards from nearly a dozen vendors, including Intel and
Qualcomm. Those are just the ones they specifically looked at—they believe the vulnerabilities affect more than 1,400 Bluetooth chips, potentially exposing billions of devices to various attack vectors.
They've dubbed these vulnerabilities BrakTooth, a combination of the Norwegian word "brak," which translates to "crash" in English, and Tooth taken from Bluetooth. Probably by coincidence (even though it is fitting), Brak also happens to be the name of a villainous character in Space Ghost, a Hanna-Barbera cartoon from the 1960s.
The researchers published all the gory technical details on GitHub, noting that BrakTooth threats range from denial of service (DoS) via firmware crashes and deadlocks in commodity hardware, to arbitrary code execution (ACE) in certain IoT devices.
Here's a demonstration of one of the exploits...
In more mild cases, these exploits can be leveraged to crash Bluetooth devices, like headphones and anything else, or otherwise make them virtually inoperable. Annoying for sure, especially if it is an expensive gadget. However, they can also pose more serious threats, like allowing an attacker to execute arbitrary code.
BrakTooth affects a wide range of devices, from adapter cards and laptops, to smartphones and practically anything with Bluetooth support. The potential attack vectors vary by device.
 Source: Singapore University of Technology and Design (via GitHub)
Source: Singapore University of Technology and Design (via GitHub)
The researchers say they disclosed their findings to the affected vendors several months ago, before publishing their data. However, the response has been mixed. A few vendors have either made patches available or are currently working on patches, while others are taking a wait-and-see approach.
"Texas Instruments has successfully replicated the security issue, however, at this stage has no plan for producing a patch. In particular, according to the Texas Instruments PSIRT team, they will consider producing a patch only if demanded by customers," the researchers state.
Yet others are selectively applying patches, it seems. According the researchers, Qualcomm is working on a fix one for a particular Bluetooth chipset, but for some of its new products, no patch is planned. This could be due to a relatively benign status of the exploit, or in some cases, because there is not enough space in ROM to issue a fix.