Alarming ASUS Driver Tool Security Bug Gives Hackers Remote Access To PCs
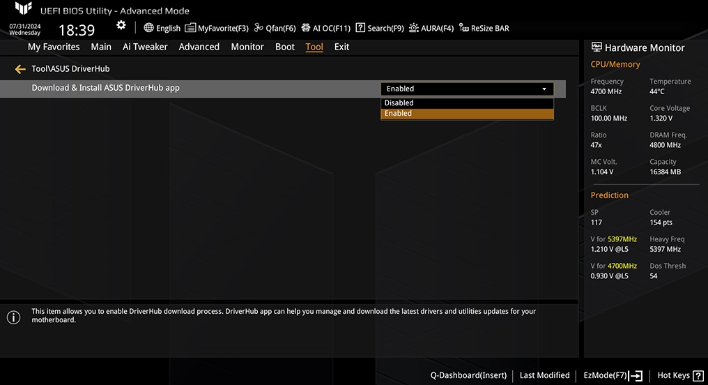
The vulnerabilities are registered with the NIST with numbers CVE-2025-3462 and CVE-2025-3463, and have scores of 8.4 and 9.6 respectively (out of 10). ASUS recommends that users immediately update DriverHub to the latest version, something that can be done directly from within the utility. Alternatively, you can disable DriverHub's automatic installation directly from within the BIOS, something yours truly always does, regardless of motherboard vendor.
Here's a simplified description of the vulnerabilities, so you can collectively facepalm with us. DriverHub operates using an open network server in the local machine. It can receive any kind of HTTP request, but it attempts to validate said request came from driverhub.asus.com. Problem #1 is that this validation isn't strict, meaning that providing driverhub.asus.com.congrats.youreowned.com as the origin works perfectly, so you can set up that domain yourself to serve malicious files.
Problem #2 now rears its ugly head: DriverHub executes any ASUS-signed .exe with administrator permissions, and without user intervention. Although the utility validates the digital signature of the installer .exe file it downloads, it doesn't do any checks for the payload files, including .ini and other executables. This means it's trivial to craft a package with a valid ASUS installer, but with a malicious payload to be run with administrator permissions.
The vulnerabilities were found by, detailed, and disclosed to ASUS by Paul aka MrBruh, a Kiwi security researcher. The response from ASUS' security folks leaves quite a bit to be desired, however. The company had apparently been made aware of the issue in February by researcher "leonjza", but took its sweet time fixing the vulnerability, which it only did in April.
ASUS' statement in the CVE reports is a little tone-deaf, too, as the Taiwanese maker says that "this issue is limited to motherboards and does not affect laptops, desktop computers, or other endpoints." This is not accurate, as any Windows installation with DriverHub is affected, regardless of whether it's a custom build, a prebuilt, or a laptop. Neither MrBruh nor leonjza saw any bounties from ASUS software department for their discoveries. As MrBruh puts it, though, this is "understandable since ASUS is just a small startup and likely does not have the capital to pay a bounty."

