Alleged Android COVID-19 Tracing App Hides Sneaky CryCryptor Ransomware Payload
A new ransomware attack is underway in Canada that targets people concerned about COVID-19 by posing as an official tracing app provided by Health Canada. ESET researchers have identified and analyzed the ransomware, known as CryCryptor, and created a decryption tool for victims. CryCryptor surfaced only a few days after the Canadian government announced that it intended to back the development of a nation-wide, voluntary tracing app called COVID Alert.
The actual tracing app from Health Canada is due to start rolling out in Ontario as soon as next month. ESET says that it informed the Canadian Centre for Cyber Security about the new threat as soon as it was identified. The below above shows the webpage for the ransomware-infested COVID-19 Tracer App. Once the victim downloads and installs the app, all the most common file types on the device are encrypted.
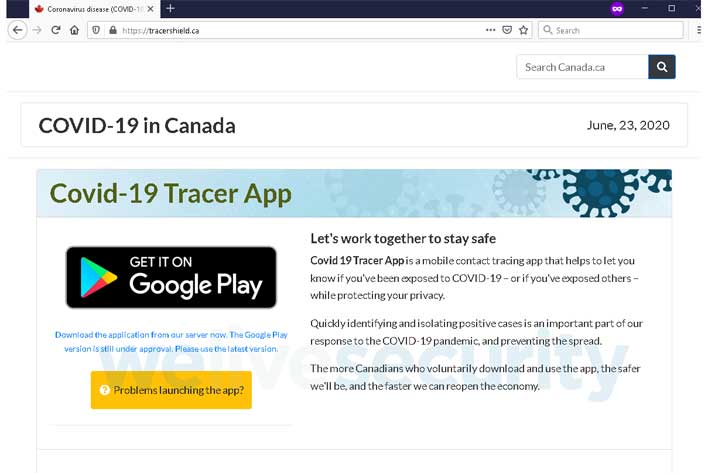
CryCryptor didn't lock the device and left behind a "readme" file with the attacker's email in every directory with encrypted files. ESET says that when the ransomware turned up on its radar, it discovered on investigation a bug of the type "Improper Export of Android Components" that MITRE labels as CWE-926 in the app. CWE-926 is a bug that allows any app installed on the affected device to launch any exported service provided by the ransomware.
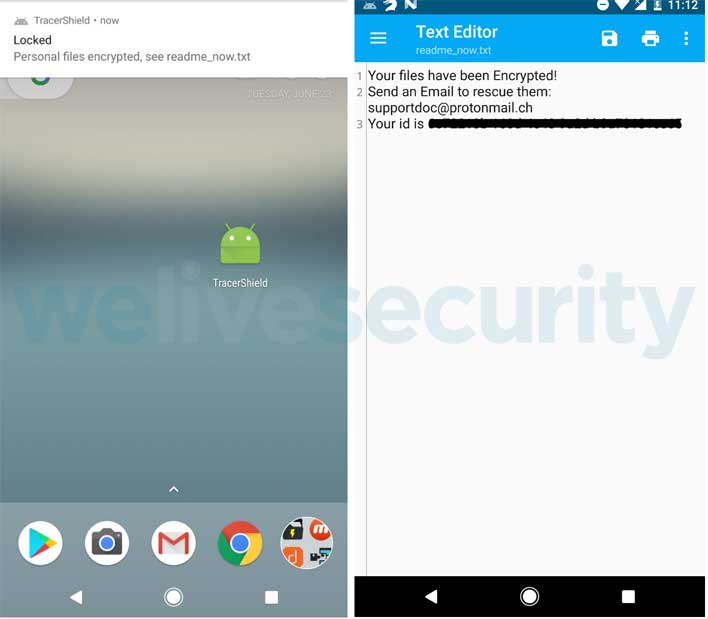
That bug is what allowed ESET to create the decryption tool, which launches the decrypting functionality that was built into the ransomware app by its creators. The image below shows the file types that the ransomware encrypts. The image above shows the message left behind with the encrypted files. ESET was able to create the decryption tool thanks to CryCryptor storing its encryption key in shared preferences. The decryption app is available for download at no cost for those impacted by the malware.
CryCryptor isn't the first malware to try and leverage fears of coronavirus/COVID-19 as a method of attacking smartphone or computer users. Microsoft announced in May that it was tracking a massive phishing malware campaign that propagated using malicious Excel spreadsheets promising coronavirus data.

