BootHole GRUB2 Bootloader Security Exploit Discovered, Affects Billions Of Windows And Linux Devices

How Does BootHole Work
The “GRand Unified Bootloader version 2”, or GRUB2, is a bootloader that is common on many Linux devices. It uses bison, a parsers generator, and flex, a lexical analyser, to “generate a parsing engine for a domain-specific language (DSL).” However, Eclypsium points out that flex and bison have “mismatched design assumptions'' which can lead to issues. In the case of BootHole, these “mismatched design assumptions” can create a buffer overflow vulnerability.A buffer overflow occurs when more data is pushed into a buffer than it can handle. This data still needs a place to go and it therefore often overflows into nearby memory spaces. This “overflow” can corrupt or overwrite the data that was originally in the memory space. Attackers can then abuse this situation to run arbitrary code and cause major problems with a device.
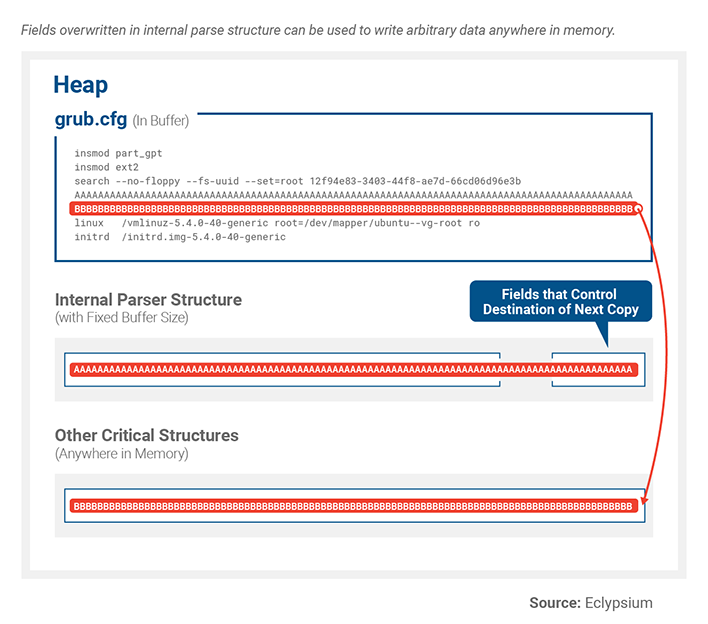
In the example provided by the researchers, Eclypsium found they could use the modified configuration file to pass a token too large for flex’s parse buffer. It called the function “YY_FATAL_ERROR()”. This threw an error code, but did not halt the execution. Flex never checks for YY_FATAL_ERROR() to return, so it continued to call and copy a token that was too large for the buffer. According to the researchers, this issue “overwrites critical structures in the heap.”
Potential Consequences and Resolution
This vulnerability can lead to major consequences. Attackers who have gained administrative privileges can execute arbitrary code and therefore take over the entire bootloader process. The attacker could run malware, replace the bootloader process with a malicious one, and gain total control over vulnerable devices.Eclypsium indicates that the attackers must already have administrative privileges. This is important to note, because you would likely already have problems if an attacker managed to get this far. However, this vulnerability is certainly cause for concern. It would further increase the attacker’s privileges and offer the ability to regain control of a system with modified bootloader in place. In turn, the attack could persist at a lower level on the system than is typically detectable while covering up evidence of its infiltration in userspace.
Eclypsium researchers also recently uncovered unsigned or unverified peripheral firmware in devices by major tech companies. Unsigned firmware not only endangers individual devices, but can threaten an entire network. The researchers were able to infect a host server and replace the system’s NIC firmware, which ultimately allowed them to monitor, modify, and redirect traffic.
Updated 7/29/2020 at 3:00pm
Below is a statement from SUSE regarding the BootHole vulnerability:
"We’re aware of the Linux vulnerability called BootHole shared by Eclypsium today, and our customers and partners can rest assured we have released fixed grub2 packages which close the BootHole vulnerability for all SUSE Linux products today, and are releasing corresponding updates to Linux kernel packages, cloud image and installation media.
Given the need for physical access to the bootloader, the most likely exposure is when untrusted users can access a machine, e.g. bad actors in classified computing scenarios or computers in public spaces operating in unattended kiosk mode. To ensure that sophisticated attackers cannot reinstall old versions of grub2, software and hardware vendors are working together. SUSE Linux Enterprise provides unprecedented reliability, stability and security to the enterprise, and we are committed to keeping our customers’ and partners’ systems up to date and ready to handle everyday business challenges."

