Some Dell Laptops Allegedly Bite Self-Signed Certificate Bait With Possible Superfish-Style Exploit
Now it looks as though Dell has a similar problem on its hands. Over the weekend, programmer Joe Nord discovered that his newly purchased Dell Inspiron 5000 notebook featured a trusted root certificate going by the name eDellRoot. Most troubling is that eDellRoot is granted with “All insurance policies” and “All applications policies” with an expiration date of 2039.
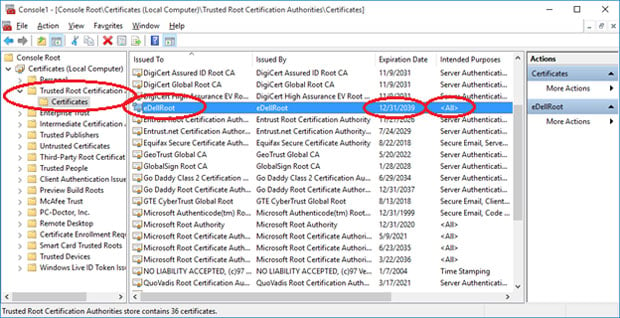
Things get even more questionable when you consider that the eDellRoot’s private key is installed on the computer. Say what?! Private keys for all intents and purposes should be locked away, safe from prying eyes. If a private key is already installed on a machine from the factory, it’s open season for malicious parties to create phony websites with seemingly legit security credentials.
“While I do know that this certificate came pre-installed on the computer and I do know that it is named ‘Dell’, I do not actually know that this certificate came from Dell Computer Corporation,” said Nord. “Root certificates are always self-signed, so all I really know is that eDellRoot says eDellRoot is legit. Where it breaks down is that the private key IS PRESENT on my computer and that means ... bad.”

reddit user crusoe has his own theory on what’s happening, writing:
This is likely for Dell support tools. But when you create a cert for internal use or tool use, you only distribute the public key portion. So people can verify it.
What Dell did here is ship the private key and installed the cert as a root cert. So anyone can use this dell root cert private to create signed certs for common domains that will look legit to most browsers.
And since the cert is on a f**kton of laptops, an attacker can set up a fake banksite that mirrors the real site, then sign the cert with the dell root cert (which dell was nice enough to include the private key for), and since the dell cert is also installed as a root, the browser will trust that fake banksite.com is the real banksite.
Although Nord was able to detect eDellRoot on his Inspiron 5000, independent verification has spotted it on XPS 13 and XPS 15 laptops as well. And even it doesn’t appear at this point that eDellRoot is an ad-serving menace, which was the primary purpose of Superfish, it still leaves Dell customers vulnerable to nefarious parties.
A representative for Dell reached out in the comments section of Nord’s blog with the following statement:
Customer security and privacy is a top concern for Dell. We have a strict policy of minimizing the number of pre-load applications and assessing all applications for their security and usability. Dell has an extensive end-user security practice that develops capabilities and best practices to best protect our customers. We have a team investigating the current situation and will update you as soon as we have more information.
We’re glad to see that Dell is on researching the matter, but it still doesn’t change the fact that this is a rather serious security lapse. We’ll be interested in hearing a full debriefing on what transpired with regards to the development and shipping of eDellRoot.

