“Malnets” Were the Cause of Most Cyber-Attacks in 2012
The web is a dangerous place, and one of the threats that emerged in 2011 was that of malnets, or malware networks, which are just what they sound like. These infrastructures are designed to last beyond a single attack and allow cybercriminals to adapt to new vulnerabilities and launch malware attacks over and over again. Malnets grew in popularity last year, and so far in 2012, they're the leading cause of cyber-attacks.
So claims Blue Coat, a provider of web security and WAN optimization solutions. According to Blue Coat, malnets are attractive to the web's seedier characters because they're adept at infecting many users with little added investment. Malnets are sometimes comprised of thousands of servers, malware infested websites, and domains spread out over large distances. Not all servers in a malnet are malicious in nature, and unlike botnets, their command and control centers are constantly changing, making them extremely difficult to track and ultimately shut down.
"The best approach you have is to take down the whole thing at once," Tim Van Der Horst, senior malware researcher with Blue Coat, told V3. "If you can find all the infrastructure nodes you could take them down, but you would be better served trying to get the real identity behind the infrastructure so you can take down the people and not just their machines."
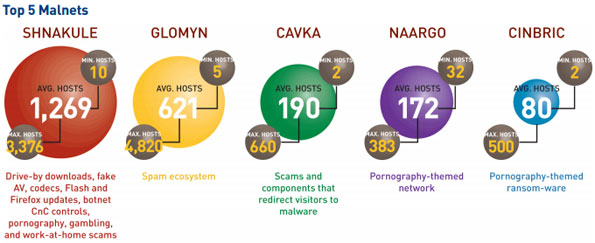
Source: Blue Coat
It's essentially a waste of time to try and take down individual systems in a network because they're easily and quickly replaced. The best defense, says Blue Coat, is a "negative day defense" that proactively blocks malnets before they launch.
"Blue Coat Security Labs maps the relationships between malnet components to identify and block new subnets, IP addresses and host names when they come online. Once the malnet infrastructure has been identified, it can be blocked at the source before attacks are launched," Blue Coat explains.
It's a self-serving strategy to Blue Coat's business model, but one reason it's an effective solution is because it doesn't matter whether the payload is a keylogger, worm, Trojan, or any other type of malware, the company explains.
So claims Blue Coat, a provider of web security and WAN optimization solutions. According to Blue Coat, malnets are attractive to the web's seedier characters because they're adept at infecting many users with little added investment. Malnets are sometimes comprised of thousands of servers, malware infested websites, and domains spread out over large distances. Not all servers in a malnet are malicious in nature, and unlike botnets, their command and control centers are constantly changing, making them extremely difficult to track and ultimately shut down.
"The best approach you have is to take down the whole thing at once," Tim Van Der Horst, senior malware researcher with Blue Coat, told V3. "If you can find all the infrastructure nodes you could take them down, but you would be better served trying to get the real identity behind the infrastructure so you can take down the people and not just their machines."

Source: Blue Coat
It's essentially a waste of time to try and take down individual systems in a network because they're easily and quickly replaced. The best defense, says Blue Coat, is a "negative day defense" that proactively blocks malnets before they launch.
"Blue Coat Security Labs maps the relationships between malnet components to identify and block new subnets, IP addresses and host names when they come online. Once the malnet infrastructure has been identified, it can be blocked at the source before attacks are launched," Blue Coat explains.
It's a self-serving strategy to Blue Coat's business model, but one reason it's an effective solution is because it doesn't matter whether the payload is a keylogger, worm, Trojan, or any other type of malware, the company explains.

