How Private Is Your Cloud? Google Could Be Indexing Your Backup Drive
If there's one thing that's beaten into the head of every computer user, it's to implement a data backup scheme. Like, right now. It's sound advice, but depending on how and where you backup your data, you could be exposing more about yourself than you care to share. Just think for a moment about the contents of your hard drive (or solid state drive) and how comfortable you would be with strangers sorting through your digital bits.
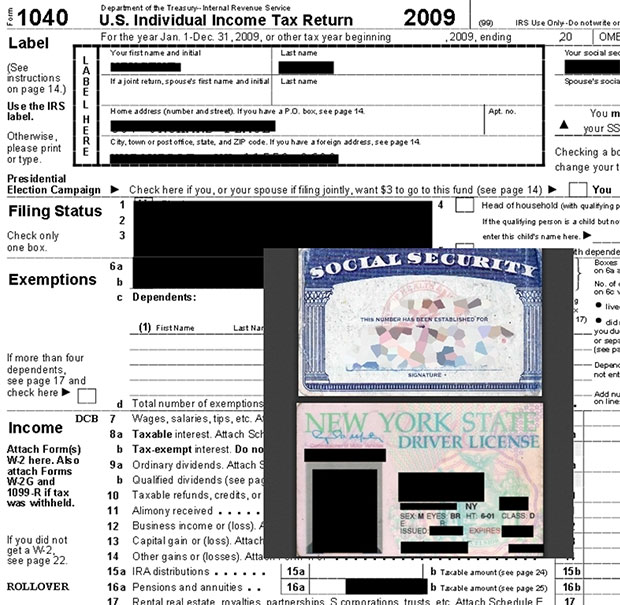
A typical storage drive might contain everything from family photos and work documents, to annual tax returns containing personal information and perhaps even naughty home videos inspired by 50 Shades of Grey. We create backups of these things because, in one way or another, they're important to us. And as a whole, they're a running snapshot of our lives, preserved in digital form, as it's done in the modern era. But are your backups truly secure?

Western Digital's My Could - Configured incorrectly, it could be anyone's cloud.
Utilizing the cloud has become the popular way of doing things, and while you may not want to store your NSFW photos and videos on third-party servers for obvious reasons, you can run out and purchase backup appliances that create a personal cloud meant just for you. We've of course reviewed many of them over the years, like Western Digital's Personal Cloud Server and, more recently, the WD My Cloud EX2 Personal Cloud Server, an updated model with more storage capacity and features.
On the surface, these devices seem to offer the best of all worlds -- cloud storage that you can access remotely, and frequent backups in case your primary storage gives up the ghost. But what if someone else could access your data? We're not talking about sophisticated (or even script kiddie) hackers, either. Depending on how you have things configured, Google and other search engines could be indexing your privately stored data, thereby making it accessible to anyone and everyone with an Internet connection.
This isn't a theory, folks. The people involved with Cross Site Security, a publication that focuses on security and risk management topics, were able to discover thousands of personals records and documents online using a few simple Google searches. They found sensitive data belonging to home users, government agencies, schools, and corporations -- everyone, in other words.
In most cases, the information was made available online because someone misconfigured a device acting as a personal cloud, or FTP was enabled on their router. In case of enabling FTP, you can usually assume it was an accident, though in some cases XSS said it was intentionally configured that way for one reason or another. Regardless of the reason(s), the result is that information was neatly indexed by Google and easily searchable.
By easily searchable, we mean you just need to look for the data, and bam, there it is for anyone to see. You don't need a password or any other type of authorization. So, say you have an external drive connected to your router and FTP is enabled. When devices acts as FTP servers using the person's IP or hostname as an address, search engines treat the external drive as a public archive.
It's pretty scary what was discovered -- very personal photos, journals, emails, passports, state IDs, tax records, financial statements, mortgage documents, birth records, customer lists, and a boatload more. There was certainly enough information available to steal someone's identity or, perhaps from a business perspective, to steal clients and gain a competitive edge.
Some of the archives went all the way back to 2004, and several were updated as recently as last month. That's over a decade worth of data. And if you're thinking these mishaps only occur on outdated hardware, think again. In at least one instance, personal data from an external drive connected to a Linksys WRT1900AC router was found, which is a current, popular model among enthusiasts. It's easy to see why someone would enable FTP services, to transfer files to and from the device remotely, but without proper security it matters very little, after the damage has been done.
XSS contacted the family who owned the router to let them know that their financial history for the past five years was viewable online. The family shared a story in return, telling of how late last year they couldn't figure out how their credit cards were being compromised within minutes of activating them.
"Now I know. [It's not] difficult when my backups were public and being indexed on Google. I got into a habit, a bad one, of storing the card info in a text file similar to many of the ones you found... When I got all of our new cards after the second time, I didn't update the text file and the problem stopped," one of the family members said.
All it takes to search for this kind of thing is standard search operators and directing Google to only display FTP results. To find out if your own data is compromised in such a manner, point your browser to ftp://[your hostname]. If you don't know your hostname, you can look it up at WhatIsMyIP.
If you do find files, there are some things you need to do to regain your privacy. Obviously you need to figure out the root cause and fix it, like disabling FTP or securing it with a strong password. But to get your data offline, you'll have to use Google's removal tool. There's also one for Bing, which shares its results with Yahoo.
Moral of the story? Don't assume your data is private, even if you're using a personal cloud. Double and triple your check settings, and when in doubt, err on the side of security over convenience.
A typical storage drive might contain everything from family photos and work documents, to annual tax returns containing personal information and perhaps even naughty home videos inspired by 50 Shades of Grey. We create backups of these things because, in one way or another, they're important to us. And as a whole, they're a running snapshot of our lives, preserved in digital form, as it's done in the modern era. But are your backups truly secure?

Western Digital's My Could - Configured incorrectly, it could be anyone's cloud.
Utilizing the cloud has become the popular way of doing things, and while you may not want to store your NSFW photos and videos on third-party servers for obvious reasons, you can run out and purchase backup appliances that create a personal cloud meant just for you. We've of course reviewed many of them over the years, like Western Digital's Personal Cloud Server and, more recently, the WD My Cloud EX2 Personal Cloud Server, an updated model with more storage capacity and features.
On the surface, these devices seem to offer the best of all worlds -- cloud storage that you can access remotely, and frequent backups in case your primary storage gives up the ghost. But what if someone else could access your data? We're not talking about sophisticated (or even script kiddie) hackers, either. Depending on how you have things configured, Google and other search engines could be indexing your privately stored data, thereby making it accessible to anyone and everyone with an Internet connection.
This isn't a theory, folks. The people involved with Cross Site Security, a publication that focuses on security and risk management topics, were able to discover thousands of personals records and documents online using a few simple Google searches. They found sensitive data belonging to home users, government agencies, schools, and corporations -- everyone, in other words.
In most cases, the information was made available online because someone misconfigured a device acting as a personal cloud, or FTP was enabled on their router. In case of enabling FTP, you can usually assume it was an accident, though in some cases XSS said it was intentionally configured that way for one reason or another. Regardless of the reason(s), the result is that information was neatly indexed by Google and easily searchable.
By easily searchable, we mean you just need to look for the data, and bam, there it is for anyone to see. You don't need a password or any other type of authorization. So, say you have an external drive connected to your router and FTP is enabled. When devices acts as FTP servers using the person's IP or hostname as an address, search engines treat the external drive as a public archive.
It's pretty scary what was discovered -- very personal photos, journals, emails, passports, state IDs, tax records, financial statements, mortgage documents, birth records, customer lists, and a boatload more. There was certainly enough information available to steal someone's identity or, perhaps from a business perspective, to steal clients and gain a competitive edge.
Some of the archives went all the way back to 2004, and several were updated as recently as last month. That's over a decade worth of data. And if you're thinking these mishaps only occur on outdated hardware, think again. In at least one instance, personal data from an external drive connected to a Linksys WRT1900AC router was found, which is a current, popular model among enthusiasts. It's easy to see why someone would enable FTP services, to transfer files to and from the device remotely, but without proper security it matters very little, after the damage has been done.
XSS contacted the family who owned the router to let them know that their financial history for the past five years was viewable online. The family shared a story in return, telling of how late last year they couldn't figure out how their credit cards were being compromised within minutes of activating them.
"Now I know. [It's not] difficult when my backups were public and being indexed on Google. I got into a habit, a bad one, of storing the card info in a text file similar to many of the ones you found... When I got all of our new cards after the second time, I didn't update the text file and the problem stopped," one of the family members said.
All it takes to search for this kind of thing is standard search operators and directing Google to only display FTP results. To find out if your own data is compromised in such a manner, point your browser to ftp://[your hostname]. If you don't know your hostname, you can look it up at WhatIsMyIP.
If you do find files, there are some things you need to do to regain your privacy. Obviously you need to figure out the root cause and fix it, like disabling FTP or securing it with a strong password. But to get your data offline, you'll have to use Google's removal tool. There's also one for Bing, which shares its results with Yahoo.
Moral of the story? Don't assume your data is private, even if you're using a personal cloud. Double and triple your check settings, and when in doubt, err on the side of security over convenience.