Massive Red October Botnet Spied On Dozens of Countries -- Including The US
Researchers with Kaspersky Labs have released information on a new botnet they've discovered that dwarfs any previous cyber-espionage efforts as far as its size, scope, and complexity. The new network, dubbed Red October, has sunk its hooks into systems worldwide. The degree of penetration varies from state to state -- in the United States, the leaks were apparently confined to diplomatic offices and embassies, while in Russia, intrusions were picked up in military installations, embassies, nuclear power plants, and in research institutions.
Elements of the Red October network have apparently been in play since 2007. Red October is the latest major cyber-espionage network detected worldwide. In 2010 a highly sophisticated worm, dubbed Stuxnet, was used to target Iran's uranium enrichment infrastructure. Once independent security researchers tumbled to its existence, they determined that it had almost certainly been engineered by the US and Israeli governments. Stuxnet was technologically advanced, leveraged multiple zero-day attacks, and used signed certificates from Jmicron and Realtek to install invisible device drivers.
Flame, which dropped in 2012, was a follow-up to Stuxnet that targeted Middle Eastern countries and particularly Iran. It didn't spread to nearly as many systems and it didn't last as long -- one of the elements of Flame's design was a "Kill" command that wiped all traces of the malware from infected systems. Once it was detected and the story went public, the malware network went dark. Flame was even more sophisticated than Stuxnet and infected 1,000 systems across Iran, Israel, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt.
Red October's command-and-control system is at least as advanced as Flame's, but it sank its teeth much deeper into nations around the world. The attackers carefully harvested sensitive data from specific systems, then stockpiled the information to deploy it when attempting to break into other computers. The system is capable of stealing data from PCs, iPhones, Nokia devices (possibly using Symbian) and Windows Mobile. It exploits holes in Cisco routers, Microsoft Word, and Excel.
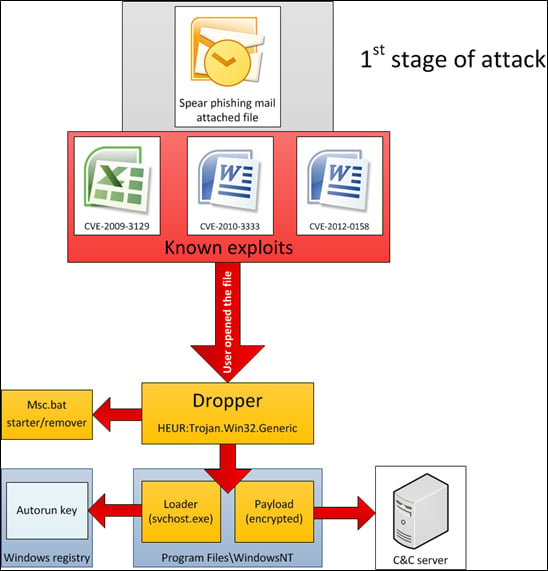
Kaspersky Lab believes that the developers of Red October spoke Russian, but noted that the modules and code they deployed was new and had never been picked up in previous cyber attacks. The goal of the infection wasn't to cause damage, as Stuxnet tried to do, but simply to gather information from as many targets as is possible. Kaspersky notes that " the attackers used exploit code that was made public and originally came from a previously known targeted attack campaign with Chinese origins. The only thing that was changed is the executable which was embedded in the document; the attackers replaced it with their own code."
Here's the countries that've been attacked:

Click to Embiggen
So whose the culprit? Unknown. True, China is the big nation not on this list, but any government smart enough to fund a project this comprehensive is smart enough to deploy it internally. China isn't exactly known for its lax internal monitoring, either. If Red October follows Flame's example, the botnet will shut down in the very near future -- leaving analysts to pick up the pieces and try to determine how many hundreds of terabytes of information were stolen from sensitive systems. The software was capable of transferring the entire contents of mobile phones, including contact list, call history, SMS messages, and browser history. It could retrieve email and file attachments accessed via Outlook using stored passwords and server information. Network information, file system data, and PDF documents were all accessed and sent back to the mother ship on compromised machines.
It'll be years before this is sorted out. Where did the information go? What was it used for?
Kaspersky doesn't know. Best guess is that it ended up on the black market.
Elements of the Red October network have apparently been in play since 2007. Red October is the latest major cyber-espionage network detected worldwide. In 2010 a highly sophisticated worm, dubbed Stuxnet, was used to target Iran's uranium enrichment infrastructure. Once independent security researchers tumbled to its existence, they determined that it had almost certainly been engineered by the US and Israeli governments. Stuxnet was technologically advanced, leveraged multiple zero-day attacks, and used signed certificates from Jmicron and Realtek to install invisible device drivers.
Flame, which dropped in 2012, was a follow-up to Stuxnet that targeted Middle Eastern countries and particularly Iran. It didn't spread to nearly as many systems and it didn't last as long -- one of the elements of Flame's design was a "Kill" command that wiped all traces of the malware from infected systems. Once it was detected and the story went public, the malware network went dark. Flame was even more sophisticated than Stuxnet and infected 1,000 systems across Iran, Israel, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt.
Red October's command-and-control system is at least as advanced as Flame's, but it sank its teeth much deeper into nations around the world. The attackers carefully harvested sensitive data from specific systems, then stockpiled the information to deploy it when attempting to break into other computers. The system is capable of stealing data from PCs, iPhones, Nokia devices (possibly using Symbian) and Windows Mobile. It exploits holes in Cisco routers, Microsoft Word, and Excel.

Kaspersky Lab believes that the developers of Red October spoke Russian, but noted that the modules and code they deployed was new and had never been picked up in previous cyber attacks. The goal of the infection wasn't to cause damage, as Stuxnet tried to do, but simply to gather information from as many targets as is possible. Kaspersky notes that " the attackers used exploit code that was made public and originally came from a previously known targeted attack campaign with Chinese origins. The only thing that was changed is the executable which was embedded in the document; the attackers replaced it with their own code."
Here's the countries that've been attacked:

Click to Embiggen
So whose the culprit? Unknown. True, China is the big nation not on this list, but any government smart enough to fund a project this comprehensive is smart enough to deploy it internally. China isn't exactly known for its lax internal monitoring, either. If Red October follows Flame's example, the botnet will shut down in the very near future -- leaving analysts to pick up the pieces and try to determine how many hundreds of terabytes of information were stolen from sensitive systems. The software was capable of transferring the entire contents of mobile phones, including contact list, call history, SMS messages, and browser history. It could retrieve email and file attachments accessed via Outlook using stored passwords and server information. Network information, file system data, and PDF documents were all accessed and sent back to the mother ship on compromised machines.
It'll be years before this is sorted out. Where did the information go? What was it used for?
Kaspersky doesn't know. Best guess is that it ended up on the black market.

