Russian Hackers Use SandWorm Windows Zero-Day Exploit To Compromise NATO, EU, US Education, Ukraine
Zero-day exploits are a nightmare for end-users and vendors alike as both groups have to scramble to patch and resolve problems. Today, Microsoft got tagged with one of the worst types of disclosures -- not only is there a vulnerability in every single shipping version of Windows, the vulnerability has been exploited for years by a team of Russian hackers, codenamed Sandworm.
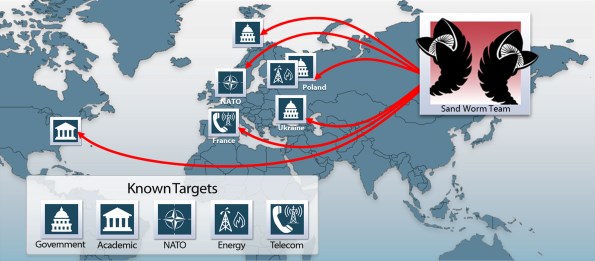
According to the iSight Partners, the Sandworm Team has been caught seeking data on the Ukrainian crisis (further undercutting the idea that the crisis in that state was anything but a Russian operation -- if such evidence were still needed), data on Western European governments, and other issues related to diplomacy, telecommunications, and energy policy. The telecommunications information makes particular sense in the wake of Edward Snowden's disclosures -- Putin likely has a keen interest in learning more about US policies and cooperation between the US government and US corporations when it comes to spying on other countries.
“This is consistent with espionage activity,” said iSight Senior Director Stephen Ward. “All indicators from a targeting and lures perspective would indicate espionage with Russian national interests.”
Ironically, Windows XP -- the one version of Windows not currently covered by any support agreements -- is the one version not impacted by this zero-day flaw.
Sandworm is believed to have been active since 2009, but the group was first detected in late 2013. The surge in recent activity paralleled rising tensions in the Ukraine in August, and Sandworm's security was ultimately compromised when it failed to properly lock down one of its own control servers operating in Germany. The group is said to have adapted commercial malware to suit its needs but there's no word on which software packages or what particular vulnerability was exploited. More details are expected to be released later this week.
Microsoft is releasing a patch today to fix the problem -- MS14-060. Admins and users will want to lock things down sharply to avoid being exploited -- if history is any indication, other groups will be quick to jump on this capability to create botnets or hijack systems.
As much as the term "cyberwar" is overused, events like this are a reminder that the term is not without applicability. The sophisticated nature of these attacks and the attackers' clear interest in foreign responses to Russian military policy are a giveaway, as is other, unspecified clues that have not been made public.
After the Snowden revelations, the NSA and other government intelligence gathering operations have often been painted as unilateral bad guys, but it's important to distinguish between spying on US citizens who have done nothing wrong and are not under suspicion of any crimes and helping to secure US infrastructure from the eyes of foreign governments. Strengthening this latter relationship has become more difficult thanks to the activities of the NSA, but discoveries like this point to the need for a coordinated security response from both the commercial and government sectors.
According to the iSight Partners, the Sandworm Team has been caught seeking data on the Ukrainian crisis (further undercutting the idea that the crisis in that state was anything but a Russian operation -- if such evidence were still needed), data on Western European governments, and other issues related to diplomacy, telecommunications, and energy policy. The telecommunications information makes particular sense in the wake of Edward Snowden's disclosures -- Putin likely has a keen interest in learning more about US policies and cooperation between the US government and US corporations when it comes to spying on other countries.
“This is consistent with espionage activity,” said iSight Senior Director Stephen Ward. “All indicators from a targeting and lures perspective would indicate espionage with Russian national interests.”
Ironically, Windows XP -- the one version of Windows not currently covered by any support agreements -- is the one version not impacted by this zero-day flaw.

Sandworm is believed to have been active since 2009, but the group was first detected in late 2013. The surge in recent activity paralleled rising tensions in the Ukraine in August, and Sandworm's security was ultimately compromised when it failed to properly lock down one of its own control servers operating in Germany. The group is said to have adapted commercial malware to suit its needs but there's no word on which software packages or what particular vulnerability was exploited. More details are expected to be released later this week.
Microsoft is releasing a patch today to fix the problem -- MS14-060. Admins and users will want to lock things down sharply to avoid being exploited -- if history is any indication, other groups will be quick to jump on this capability to create botnets or hijack systems.
As much as the term "cyberwar" is overused, events like this are a reminder that the term is not without applicability. The sophisticated nature of these attacks and the attackers' clear interest in foreign responses to Russian military policy are a giveaway, as is other, unspecified clues that have not been made public.
After the Snowden revelations, the NSA and other government intelligence gathering operations have often been painted as unilateral bad guys, but it's important to distinguish between spying on US citizens who have done nothing wrong and are not under suspicion of any crimes and helping to secure US infrastructure from the eyes of foreign governments. Strengthening this latter relationship has become more difficult thanks to the activities of the NSA, but discoveries like this point to the need for a coordinated security response from both the commercial and government sectors.

