$300 Wireless Encryption Key Stealing Device Is A Real PITA
Researchers at Tel Aviv University have developed a tool for stealing decryption keys from laptops. What sets the tool apart from other hacking tools is that it is untethered: it doesn’t need to connect to the target laptop (nor a hacker’s laptop) to operate. And, it’s small. As researchers point out, it could even be hidden in pita bread.
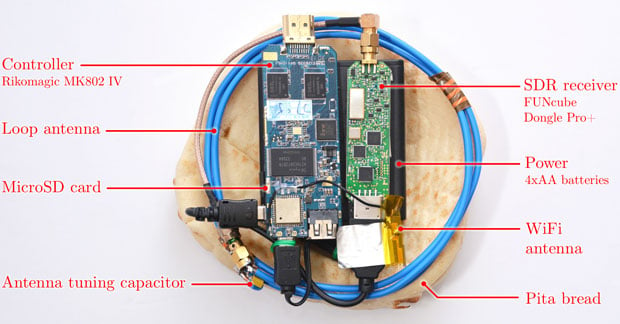
The Portable Instrument for Trace Acquisition (PITA) makes use of inexpensive equipment and can breach ElGamal and RSA encryptions, according to the researchers. They build the PITA with software defined radio (SDR) USB dongle and a similar device with a standard radio receiver. To perform the attack, you hold the loop antenna close to the laptop while your recording device records the signal. If standing near a particular laptop with a pita in your hand would be awkward, you could use a microphone to access the decryption keys from "several meters." Not that standing a few feet away with a microphone would look any less weird.
The tests, which were run at the Laboratory for Experimental Information Security (LEISec), showed that sending ciphertexts to laptops could trigger certain values in decryption software, which would make the laptop’s electromagnetic field fluctuate. The fluctuations need to be recorded so that signal analysis can be performed by a computer.
The attacks affect GnuPG encryption software, but the researchers worked with GnuP developers to create countermeasures that were adopted in GnuPG 1.4.19 and Libgcrypt 1.6.3 prior to the release of the description of the PITA attack. The countermeasures are built into the software, which is more effective than relying on manufacturers to implement hardware redesigns, the researchers believe. In any event, it solves the problem immediately, rather than requiring new hardware.
The Portable Instrument for Trace Acquisition (PITA) makes use of inexpensive equipment and can breach ElGamal and RSA encryptions, according to the researchers. They build the PITA with software defined radio (SDR) USB dongle and a similar device with a standard radio receiver. To perform the attack, you hold the loop antenna close to the laptop while your recording device records the signal. If standing near a particular laptop with a pita in your hand would be awkward, you could use a microphone to access the decryption keys from "several meters." Not that standing a few feet away with a microphone would look any less weird.

Image credit: Tel Aviv University
The tests, which were run at the Laboratory for Experimental Information Security (LEISec), showed that sending ciphertexts to laptops could trigger certain values in decryption software, which would make the laptop’s electromagnetic field fluctuate. The fluctuations need to be recorded so that signal analysis can be performed by a computer.
The attacks affect GnuPG encryption software, but the researchers worked with GnuP developers to create countermeasures that were adopted in GnuPG 1.4.19 and Libgcrypt 1.6.3 prior to the release of the description of the PITA attack. The countermeasures are built into the software, which is more effective than relying on manufacturers to implement hardware redesigns, the researchers believe. In any event, it solves the problem immediately, rather than requiring new hardware.

