Security Research At The Hague: The Mobile Malware Threat
The Hague Security Delta
One of the more interesting stops on our recent trip to Amsterdam was at The Hague Security Delta. For those of you who might not be aware, The Hague is the name of the government seat of the Netherlands (and yes, the article is capitalized). The Hague Security Delta (HSD) is the official title of a collaborative effort between Netherlands businesses, the government, and multiple research institutions to identify emerging security threats, share best practices, and foster collaboration between industry, governments, and universities.
One of the most interesting topics that came up during our visit was the issue of mobile network security, particularly now that Edward Snowden has let the cat somewhat out of the bag. Since his initial allegations shone light on the various activities of government spy agencies, we've seen an increased level of scrutiny on activities that were formerly flying under the radar.
One point that the Netherlands' officials made repeatedly during our conversation is that the company is the "digital gateway" to Europe. In other contexts, this might seem like hubris -- but once you look at the arrangement of undersea cables between the US and Europe, it makes a lot more sense.
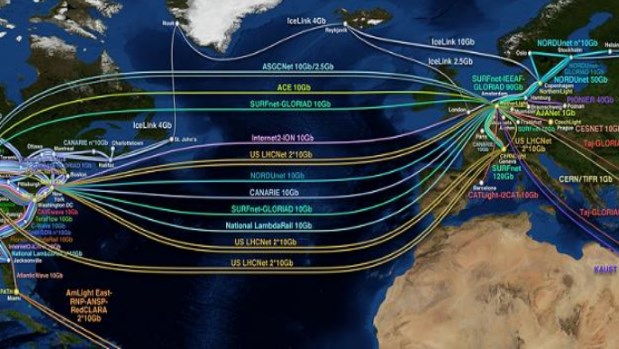
The Netherlands is far from the only transatlantic connection hub between the US and Europe, but it certainly accounts for a significant chunk of total cable capacity. One of the brainchildren of the Security Delta is the creation of what it calls a Trusted Networks Initiative -- a program that would allow direct denial of service attacks originating from specific countries to be cut off.

This rather cartoonish image still gets the point across. By creating a network "bridge" that can be raised and lowered, the idea is that content and visitors can be cleanly isolated from the bad actors launching an attack. There's an intrinsic assumption here -- specifically, the idea that attackers are gathered into a group of systems that can cleanly be split from the so-called "Trusted" networks that would continue to operate.
When I asked the project leads if this program could also be used to facilitate censorship, they seemed surprised that anyone would even raise the question. I can believe that as a matter of principle, the Netherlands is scarcely seeking to emulate the rules of mainland China or its Great Firewall. Furthermore, it makes perfect sense that in an age where state-sponsored attacks are on the rise, countries are going to seek ways to protect their own internal networks from this kind of coercive attack. But the similarities between "Protect ourselves from outside attack" and "Create trusted networks that double as censorship systems" means that this kind of research will always be a double-edged sword.
One of the most interesting topics that came up during our visit was the issue of mobile network security, particularly now that Edward Snowden has let the cat somewhat out of the bag. Since his initial allegations shone light on the various activities of government spy agencies, we've seen an increased level of scrutiny on activities that were formerly flying under the radar.
One point that the Netherlands' officials made repeatedly during our conversation is that the company is the "digital gateway" to Europe. In other contexts, this might seem like hubris -- but once you look at the arrangement of undersea cables between the US and Europe, it makes a lot more sense.

The Netherlands is far from the only transatlantic connection hub between the US and Europe, but it certainly accounts for a significant chunk of total cable capacity. One of the brainchildren of the Security Delta is the creation of what it calls a Trusted Networks Initiative -- a program that would allow direct denial of service attacks originating from specific countries to be cut off.

This rather cartoonish image still gets the point across. By creating a network "bridge" that can be raised and lowered, the idea is that content and visitors can be cleanly isolated from the bad actors launching an attack. There's an intrinsic assumption here -- specifically, the idea that attackers are gathered into a group of systems that can cleanly be split from the so-called "Trusted" networks that would continue to operate.
When I asked the project leads if this program could also be used to facilitate censorship, they seemed surprised that anyone would even raise the question. I can believe that as a matter of principle, the Netherlands is scarcely seeking to emulate the rules of mainland China or its Great Firewall. Furthermore, it makes perfect sense that in an age where state-sponsored attacks are on the rise, countries are going to seek ways to protect their own internal networks from this kind of coercive attack. But the similarities between "Protect ourselves from outside attack" and "Create trusted networks that double as censorship systems" means that this kind of research will always be a double-edged sword.






