New MS Security Report Shows Infections Down, Malicious Java Exploits Way Up
Today, Microsoft released its detailed security report covering the latter half of 2010. Industry tends in general are positive—vulnerability disclosures in 2010 fell 16.5 percent from their 2009 levels and approximately 35 percent from 2006. Microsoft's own share of the vulnerability pie rose from 4.5 percent in 2009 to 7.2 percent in 2010; the company claims this is largely because industry disclosures fell so sharply in just one year.
The general decline in disclosures hides sharp changes in the nature of the exploits roaming the Internet. From the report:
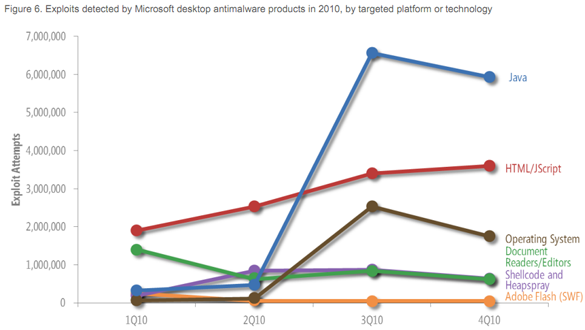
The HTML/J-Script specific exploits targeted iFrames (a general favorite), while IE-specific vulnerabilities rose steadily all year. Again, these aren't problems with current products—the exploits targeted CVE-2010-0806, "a vulnerability that affects Internet Explorer versions 6 and 7 running on versions of Windows earlier than Windows 7 and Windows Server 2008 R2. Microsoft has issued Security Bulletin MS10-018 to address this vulnerability."
To Build A Better Stupid

The last two graphs we're presenting here detail various common attack vectors as well as the two most common reasons for data theft. As you can see, there's actually a brief moment in 2010 when "Attacks" account for 50 percent of breach incidents. "Negligence" promptly slapped the upstart hackers; the miscreants cowered in hiding through the end of the year.

Combine the data from these two graphs, and you realize that data theft and so-called "hacks" are driven by a virulently evolving strain of Stupid. It's been a generation since computers began to be common features of the workplace; yet MS notes: "Malicious incidents (those involving "hacking" incidents, malware, and fraud) routinely account for less than half as many incidents as negligence (involving lost, stolen, or missing equipment; accidental disclosure, or improper disclosure...improper disposal of business records accounts for a significant portion of incidents.
Consider the recent hacks that took down Sony's PlayStation Network. The company was deliberately targeted and illegally attacked—nothing changes that—but it's hard to feel entirely sorry for Sony, considering the company's Apache site licenses were so old, they're signed by Cochise. It's ironic that for all the patching, disclosure, and heuristic algorithms in the world, we haven't found a way to stop employees from tossing sensitive data in the common trash can.
The general decline in disclosures hides sharp changes in the nature of the exploits roaming the Internet. From the report:
Malware written in Java has existed for many years, but attackers had not focused significant attention on Java vulnerabilities until somewhat recently. In 3Q10, the number of Java attacks increased to fourteen times the number of attacks recorded in 2Q10, driven mostly by the exploitation of a pair of vulnerabilities in version of the Sun (now Oracle) JVM: CVE-2008-5353 and CVE-2009-3867. Together, these two vulnerabilities accounted for 85 percent of the Java exploits detected in the second half of 2010.The company also notes that document reader exploits fell in Q2 and remained low thereafter, while OS exploits jumped in Q3 thanks to a pair of (unspecified) Windows vulnerabilities. The leap in Java exploits is so dramatic, it implies that problems in this one area may have thrown off results for the entire year.

The HTML/J-Script specific exploits targeted iFrames (a general favorite), while IE-specific vulnerabilities rose steadily all year. Again, these aren't problems with current products—the exploits targeted CVE-2010-0806, "a vulnerability that affects Internet Explorer versions 6 and 7 running on versions of Windows earlier than Windows 7 and Windows Server 2008 R2. Microsoft has issued Security Bulletin MS10-018 to address this vulnerability."
To Build A Better Stupid

The last two graphs we're presenting here detail various common attack vectors as well as the two most common reasons for data theft. As you can see, there's actually a brief moment in 2010 when "Attacks" account for 50 percent of breach incidents. "Negligence" promptly slapped the upstart hackers; the miscreants cowered in hiding through the end of the year.

Combine the data from these two graphs, and you realize that data theft and so-called "hacks" are driven by a virulently evolving strain of Stupid. It's been a generation since computers began to be common features of the workplace; yet MS notes: "Malicious incidents (those involving "hacking" incidents, malware, and fraud) routinely account for less than half as many incidents as negligence (involving lost, stolen, or missing equipment; accidental disclosure, or improper disclosure...improper disposal of business records accounts for a significant portion of incidents.
Consider the recent hacks that took down Sony's PlayStation Network. The company was deliberately targeted and illegally attacked—nothing changes that—but it's hard to feel entirely sorry for Sony, considering the company's Apache site licenses were so old, they're signed by Cochise. It's ironic that for all the patching, disclosure, and heuristic algorithms in the world, we haven't found a way to stop employees from tossing sensitive data in the common trash can.

