Google Security Researchers Detail How Hijackers Manually Attack And Compromise Online Accounts
Here's a not-so-fun fact for your Friday workday -- there are 9 incidents per million users per day involving "manual hijacking," which is when professional attackers spend considerable time exploiting a single victim's account, often causing financial losses, Google says. Though they're not the most prominent types of attack, they're often severe in nature.
This is one of the things that Google monitors, and by studying this type of hacker, the company has been able to improve its defenses against not only manual hijacks, but all kinds of hijacking. According to Google, it's been able to reduce overall hijackings by more than 99 percent over the last few years.
Nevertheless, if a professional attacker targets you and is willing to put so much effort into gaining access to your accounts, is there really anything you can do? The answer is yes, and it starts with understanding what methods they use. Google says most hijackers infiltrate accounts through phishing.
Source: Google
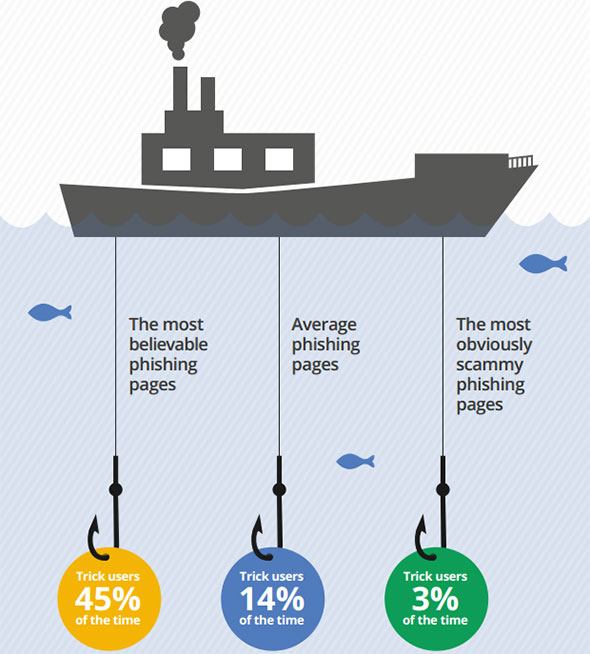
"Most of us think we’re too smart to fall for phishing, but our research found some fake websites worked a whopping 45 percent of the time," Google says. "On average, people visiting the fake pages submitted their info 14 percent of the time, and even the most obviously fake sites still managed to deceive 3 percent of people. Considering that an attacker can send out millions of messages, these success rates are nothing to sneeze at."
Hackers are quick to act, too -- around 20 percent of hijacked accounts are accessed within 30 minutes of the victim's login info being compromised. Once inside your account, the attacker typically changes your password and looks at your account details.
One advantage working in your behavior is that Gmail blocks most spam an phishing emails, assuming you use Gmail. Nevertheless, you have to be wary of all messages, including those seemingly sent from friends and family members. If their accounts have been compromised, an attacker will send emails to their contacts.
There's quite a bit to digest, and if you're in need of some reading material to end your work week, check out the full 12-page study (PDF).
This is one of the things that Google monitors, and by studying this type of hacker, the company has been able to improve its defenses against not only manual hijacks, but all kinds of hijacking. According to Google, it's been able to reduce overall hijackings by more than 99 percent over the last few years.
Nevertheless, if a professional attacker targets you and is willing to put so much effort into gaining access to your accounts, is there really anything you can do? The answer is yes, and it starts with understanding what methods they use. Google says most hijackers infiltrate accounts through phishing.

Source: Google
"Most of us think we’re too smart to fall for phishing, but our research found some fake websites worked a whopping 45 percent of the time," Google says. "On average, people visiting the fake pages submitted their info 14 percent of the time, and even the most obviously fake sites still managed to deceive 3 percent of people. Considering that an attacker can send out millions of messages, these success rates are nothing to sneeze at."
Hackers are quick to act, too -- around 20 percent of hijacked accounts are accessed within 30 minutes of the victim's login info being compromised. Once inside your account, the attacker typically changes your password and looks at your account details.
One advantage working in your behavior is that Gmail blocks most spam an phishing emails, assuming you use Gmail. Nevertheless, you have to be wary of all messages, including those seemingly sent from friends and family members. If their accounts have been compromised, an attacker will send emails to their contacts.
There's quite a bit to digest, and if you're in need of some reading material to end your work week, check out the full 12-page study (PDF).

